Windows 8 comes with the option to pre-provision the disk for use with BitLocker, allowing only the used-space to be encrypted, thus reducing the encryption time a lot.
Problem occur when enterprises want to use the Microsoft Bitlocker Administration and Monitoring (MBAM) toolkit from the Microsoft Desktop Optimization Pack (MDOP) to store BitLocker recovery keys, and track compliance. MBAM 2.0 sp1 does not support used-space encryption as per the release notes, forcing enterprises to either drop MBAM or perform full encryption of the disk, which can be a time consuming task depending on disk size and CPU performance.
After spending quite some time investigating this, reading multiple blogs, articles etc. only to find other people with the same dilemma, and vague hints to how to overcome this, I managed to get this to work.
The scenario:
- Windows 8.1 is deployed using bare-metal deployment through SCCM 2012R2
- Hardware has been prepared, meaning that the TPM has been enabled and activated in BIOS
- MBAM servers have been installed and integrated into SCCM as per the documentation
- MBAM Group policy’s has been created, forcing Bitlocker for the OS drive, and backing up TPM password to Active Directory.
When deploying a new computer using the bare-metal task sequence, we want the OS disk to be pre-provisioned using used-space-only encryption, allowing for encryption as image is applied to disk.
Once the Windows 8 image has been installed, we want MBAM to set protectors, and backing up the recovery keys to Active Directory.
TPM backup
After trying several different methods for having MBAM back up the TPM Hash to the MBAM database , I would always end up with either missing the TPM hash or the TPM being in legacy mode.
If MBAM is to backup the hash key, it has to be the owner of the TPM and this will force the TPM into legacy mode in Windows. This is not a scenario that I like due to possible 3.rd party security solutions relying on the TPM.
As a result of this I opted for the solution where Windows takes ownership of the TPM, and the Hash key is backed up to Active Directory.
The Task Sequence
Ok enough background information, lets look at the implementation I ended up with.
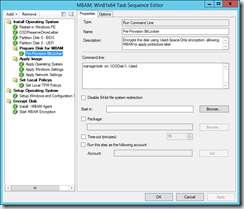
First step is to pre-provision the disk. For this we can use the “Manage-bde –on” command.
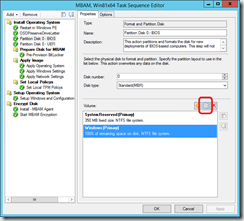
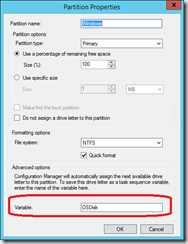
I use the %OSDisk% variable to specify the disk to be encrypted. This variable must be set in the Partition Disk step:
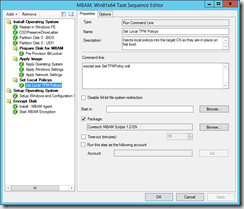
Next comes the part that was causing me all the headaches, we need to inject local policies into the target OS so these are in place at first boot. If these settings are not set, backup of the TPM to Active Directory will fail, and sometimes lead to TPM being left in legacy mode.
The SetTPMPolicy.wcf script contains a subset of the settings that are specified in the BitLocker and MBAM Group Policy’s´for forcing AD backup and encryption type.
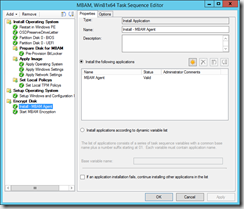
Once the operating system is installed, we need to install the MBAM agent and trigger it to apply protectors and backup the recovery keys.
The installation of the agent is performed by an application that deploys the MBAMClient.msi located on the MDOP installation media.
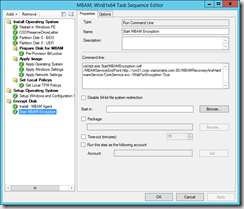
Finally, to trigger MBAM to apply protectors we execute a script that will stop the MBAM agent service and set local registry keys to specify MBAM endpoint, and disable the delayed startup, before starting the service again. MBAM will now read its temporary settings from registry, and finalize the encryption and backup the recovery keys.
The StartMBAMEncryption.wsf script that I use is inspired by the script originally made by David Hornbaker from the Deployment Guys, and later modified by alexsemi (found here: The Deployment Guys and here: AlexSemi’s Blog).
One of the modifications that I have made, is to make the script wait for the encryption and backup to complete before exiting. I experienced several occasions where a reboot just after starting the encryption would cause the backup to fail.
The scripts used in this task sequence is attached to this post, and can be downloaded and placed in a package along with the ZTIUtility.vbs script from the MDT 2013 toolkit.
Scripts can be downloaded here: [download id=”199″]
Conclusion
Although not supported by MBAM directly, it is possible to use MBAM along with Used-Space-Only encryption.

Hi Henrik,
I am looking for a method to pre provision MBAM & store the recovery keys to the MBAM Database. I have a few questions –
1) Can your method be modified to allow the backup of recovery keys to the MBAM database?
2) Will this work for Windows 7?
3) Our current infrastructure is ConfigMgr 2012 SP1, MBAM 2.0 (no service pack) and MDT 2012 Update 1. Would your method work in sure an environment?
I’m keen to understand this, so thanks in advance
Hi Tony,
The method I use does perform a backup of the BitLocker recovery keys to the MBAM database, only the TPM hash is backed-up to Active Directory.
Used-Space-only encryption is a new feature of BitLocker introduced in Windows 8, and therefore you can not use this feature in Windows 7.
You will though be able to pre-provision BitLocker, and have MBAM perform backup of BitLocker recovery keys. This works well with SCCM 2012 and MBAM 2.0.
You should be able to use the same task sequence steps, only modifying the manage-bde command skipping the -Used argument as it is not supported on Windows 7.
Used-Space-only encryption is a new feature of BitLocker introduced in Windows 8, and therefore you can not use this feature in Windows 7.
You will though be able to pre-provision BitLocker, and have MBAM perform backup of BitLocker recovery keys. This works well with SCCM 2012 and MBAM 2.0.
You should be able to use the same task sequence steps, only modifying the manage-bde command skipping the -Used argument as it is not supported on Windows 7.
Greetings Henrik,
I am going through the same pain but I have an additional issue. On our laptops we have both a C and D drive. I can get MBAM to save the C drive recovery key to the database but not D with pre-provisioning. It appears MBAM is only interested in TPM protected drivers which D cannot be. I am still trying out things to achieve this as we can get MBAM to save the D drive keys if we do a full encryption (yuck!).
btw – We do pre-provisioning on Windows 7. Whilst it is true that the “used” parameter is not supported on the Manage-Bde -on command within Windows 7, you can do this this within WINPE 4.0 or greater (as its Windows 8) in a task sequence that installs Windows 7. We do it!
Hi David,
Nice to hear that I’m not the only one who has struggled getting this to work.
First of all, thanks for the heads-up on the Windows 7 issue, of course it depends on the version of WinPe that you use. I have not worked with Windows 7 for quite some time now so I haven’t really tested it but now I have to
I have not had the need to encrypt additional drives yet, but I would believe that it should work with MBAM as well…
The StartEncryption script needs to be modified though, as it is hardcoded to only handle the C: drive.
If you pre-provision the drive, in the same way as the C: drive and modify the script to add protectors to the D drive I would believe that it should work.
Have a look at line 125-134, this loop adds the protector to the C: drive
Line 182-184 and 196 enables the protector
The for loop in line 202-213 is only for the C: drive as it sets the TPM protector, which can only be used on C: as you mention your self.
I will try to get the time to create a new post with these changes in the near future.
Did you manage to get this working dor D: as well as C:
Hi David,
I followed exactly the same process for implementing MBAM bitlocker encryption on Windows 8.1 64 bit task sequence using SCCM 2012 R2.
In the Pre-provisioning bitlocker step, I tried all these, even with disabling 64 bit file redirection
1. Manage-bde –on %OSDisk% -UsedSpaceOnly
2. Manage-bde –on %OSDisk% -Used
But I am getting error “The operating system reported error 2147942487: The parameter is incorrect.” in status message.
However the inbuilt step of Pre-provioning bitlocker is showing success
Initializing TPM…
Tpm is enabled
Tpm is activated
Tpm is owned
Tpm ownership is allowed
Tpm has compatible SRK
Tpm has EK pair
Initial TPM state: 63
Searching for next available system volume:
Used Space Only encryption is now in progress..
Again for Set Local Policies step, it is not going past this error message at all in the status message.
The operating system reported error 1: Incorrect function.
Initially I tried with wscript.exe SetTPMPolicy.wsf, then I tried with cscript.exe SetTPMPolicy.wsf
but the same message is coming.
MBAM agent is getting installed and the Start Encryption command line as suggested by you is also successful.
At the end, C: drive is fully encrypted once the full task sequence was completed.
can you please suggest, what i need to do to get past those error message.
Thanks in advance.
Sorry David, the questions was for Henrik.
Hi Henrik, could you please respond to my queries above.
@Shakir,
Error 2147942487 from manage-bde translates to “The key protector has an invalid format.” or “The EncryptionMethod parameter is provided but is not within the known range or does not match the current Group Policy setting.”
-This could indicate that TPM settings in BIOS is invalid. have you tried to reset the TPM chip?
-Make sure that the %OSDisk% variable is assigned to the Windows partition in the format step.
-Make sure your group policy for MBAM/Bitlocker allows for the use of TPM only.
to troubleshoot further, try creating a task sequence that is as clean as possible, and deploy the install.wim file as OS. I have used this method at several customers, and never had any problems like you are facing…
I keep getting “Failure (10005): 1: Loading Offline registry hive from : Windowssystem32configsoftware” when running SetTPMPolicy.wsf. I’ve also tried running the script manually from both Windows PE and Windows 8.1 with the same error.
Any ideas?
@Joe
Sorry for the late answer, but been offline for a few days…
It seems that you are missing a drive reference, so the script can´t locate the hive.
Make sure that you execute the script in the task sequence after image is applied, but before rebooting to Windows mini setup. The Script relies on the task sequence variable OSDisk to resolve the drive with the applied image, so make sure this is set as well.
Hi Henrik,
One small query about MBAM,
do we have any option for start the Encryption for C and D drive at same time in MBAM 2.0?
Earlier in MBAM 1.0 having this option
Reason is MBAM 2.0 client installed machine we need to wait until completing the C drive encryption to start D drive encryption.
Thanks in Advance,
Mathew
Greetings! The TPM script requires backing up to AD. With current MBAM solutions we don´t use AD recovery at all. Is there any way to create similar TPM script without AD recovery requirement? We do not modify AD at all for Bitlocker.
Hi Mr. Henrik,
Thank you for the great post. According to the following thread in the MBAM forum (https://social.technet.microsoft.com/Forums/en-US/6cbf51f8-76e9-4689-8541-c8c9e505689b/mbam-agent-key-escrow-issue-after-preprovisioning-bitlocker-in-sccm-ts?forum=mdopmbam), the MBAM agent will not automatically regenerate the recovery key if the manage-bde command is used to set TPM/Numerical Password key protectors. As I understand, the StartMBAMEncryption.wsf script also uses manage-bde command inside. Have you had the chance to verify if the MBAM agent regenerates the recovery key for the system that has been encrypted using the StartMBAMEncryption.wsf script? Personally, I do not think this is critical if the original recovery key is retained in the MBAM database although the static key is less secure than dynamic key that MBAM should regenerate.