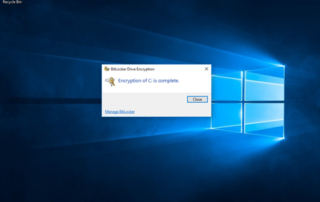
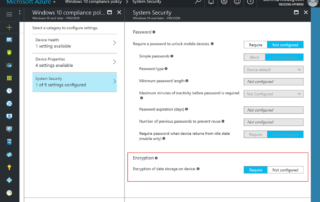
Intune: Use PowerShell management extension to enable BitLocker on a modern managed Win10 device
I wrote a blog post back in April on "how to manage BitLocker on a Azure AD Joined Windows 10 Device managed by Intune", where I also wrote a PowerShell script to automate the encryption process for the day that we would get PowerShell support in Intune. Well Microsoft announced in September the Management extension for Intune which basically lets you deploy PowerShell scripts via. Intune to Windows 10 devices. My co-worker Peter Daalmans wrote a great blog post about it right after, where he explained in more detail about the extension. I have a link for that post at [...]