Lately I have been working a bit with UNIX/Linux in SCOM 2012. I feel about it almost the same way I feel about certificates. Usually it works fine, but anything wrong or any errors, and it can quickly be a time consuming process.
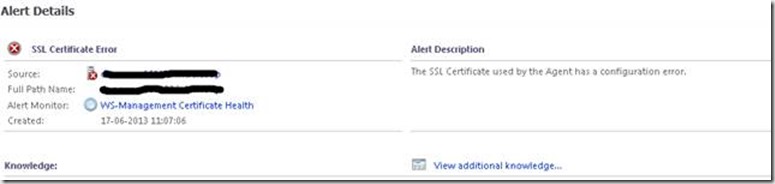
Today I ran into the “SSL Certificate Error”. I got this alert on servers already monitored for a week, so I seemed a little strange. I had also done the scxconfig –export and –import, so I couldn’t see how it should be a certificate issue. Also, the Product Knowledge was of very little help, as it just suggested what every single blog/comment on Technet suggests: check DNS, check accounts, check…
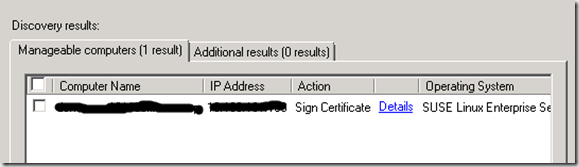
The only way I know that the certificate is handled automatically is when installing the agent through the Discovery Wizard. So I went on and pressed “Discover”, which gave me this outcome:
I clicked “Manage” and short after it failed with this message:
Failed to sign kit. Exit code: 1
Standard Output: Failed to start child process ‘/etc/init.d/scx-cimd’ errno=13
RETURN CODE: 1
Standard Error: cp: cannot create regular file `/etc/opt/microsoft/scx/ssl/scx.pem’: Permission denied
Exception Message:
Doesn’t really make sense to a non-Linux guy like me, but the “Permission denied” is universal. I passed the message on to a Linux guy, who could make sense out of it. He fixed it with this:
RunAsAccount@servername:~> ls -l /etc/opt/microsoft/scx/ssl/scx-host-servername.pem
-r–r–r– 1 root root XXX Jun 17 11:06 /etc/opt/microsoft/scx/ssl/scx-host-servername.pem
RunAsAccount@servername:~> sudo chown RunAsAccount /etc/opt/microsoft/scx/ssl/scx-host-servername.pem
RunAsAccount@servername:~>
I have renamed the name of the SCOM service account on the Linux as well as the Linux server. After the Linux guy doing his magic I could successfully sign the certificate, and minutes later my Linux machine was healthy again.
Happy re-signing certificates’ing!
FYI, those commands are literally just changing the user ownership on the certificate file, to be in the same of the SCOM agent account. It was probably owned by the wrong account.