I’m often asked if its possible to use the USMT 4.0 hardlinking (keep backup file on the OS Disk), in combination with bitlocker..
I guess the reason for the question is, that one might think!
- How can I do a backup of a machine, and keep the files on the encrypted drive, and then be able to reinstall that same drive with a new OS, ginning access to the backup that was on the encrypted drive?
- How do I stage WinPE on the Bitlocked disk, and then gain access to that same disk for the OS installation part when inside WinPE.Or at least something like that?
The thing is, that not only is it possible, it will also save you the time it takes to encrypt the drive again, because, even though a new OS is applied to the disk, the encryption is still in effect…
So lets look at the scenarios….
If we have a machine, where bitlocker is enabled, and we choose to do a bare metal installation, where the disk is formatted, we will have to make sure to create the 300+ bitlocker partition, and then start encrypting the entire drive once again…
We could also do a refresh scenario, where the TS is advertised to the running XP/vista/win7 client, and executed from there. In that case, running a standard wizard build TS (unless its a MDT Task Sequence, and I’ll get back to that), the TS is either going to backup to the SMP (state migration point), or boot directly to WinPE depending on whether or not the USMT part is enabled. either way, the TS I going to fail, because we cannot stage WinPE on a locked drive, and therefore, not boot into WinPE!
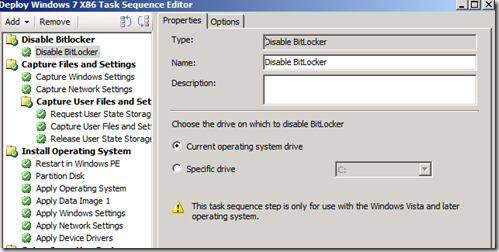
This small bump in the road, is easily fixed though, by adding an extra step to the TS, that temporarily disables Bitlocker
By adding this step, bitlocker is temporarily disabled, and access to the locked drive will become available, enabling the TS to put WinPE on to the disk.
Be aware though, that by default SCCM cannot stage WinPE on a bitlocked harddisk if it is in the process of being either encrypted or decrypted. There is however no problem, if the disk is fully de-or encrypted. For testing scenarios where you might be I the proses of doing exactly that, WinPE can be stage on the Bitlocker Boot partition if it has a drive letter assigned, and has at least 500 MB free space.
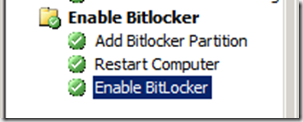
Once WinPE is on the disk, the computer will reboot, pick up the TS, and format the drive. You then have to create the Bitlocker boot partition again, enable bitlocker on the OS drive, and do the encryption all over again!
With Hardlink!
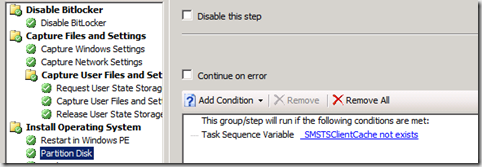
Now, lets say that we choose to use hardlinking. In that case all the backup data is stored locally on the disk, which means, we cannot format it, or the data will be lost.. The standard Wizard build TS already has taken this into account, like you se in the picture beneath.
As you can see, The partition step will only run if _SMSTSClientChache, does not exist. When doing hardlink USMT, this variable will be set, and the TS will skip the partitioning step. The “Apply Operating system Image” step will by default clean the disk, but not format (basically leaving the USMT data intact). The Clean/wipe of the disk also keeps the disk bitlocked, so all you will have to do is enable bitlocker again at the end of the task sequence, and the disk will be locked, and fully encrypted straight away.
Note: If you, like me, have a step that creates the Bitlocker boot partition, just put a “continue on error” on it, as it will fail if the boot partition is already there!
So, what can be concluded from this! Well the most important thing is that Hardlink and Bitlocker works perfect together, but also that it actually gives you the benefit of not having to run the entire process of locking down the disk again, as it is already locked… So if you are reinstalling machines with bitlocker enabled, and you do not do and USMT or use the SMP to store the data, make sure to do refresh, and set options on your partition step so that the disk is not formatted… If you use a MDT build TS, this is default, and so is hardlinking if you have the step “Determine Local or Remote UserState”

[…] Read his full post here. […]
This is a great post.
One question I have is exactly how the third step from the end ‘Add Bitlocker Partition’ is performed.
Also, what if you want to run USMT Hardlink from WinPE without booting into the OS? We do that currently, but I’m thinking there is no option for this any longer, because there is no way to Disable Bitlocker from WinPE?
The step is just a run command line – “BdeHdCfg -target default -quiet”. It will create a 300 MB partition for BDE to use. check full syntax here http://technet.microsoft.com/en-us/library/ee732026(WS.10).aspx
About disabling BDE from within WinPE, then no that is not possible (What would be the point of Bitlocker if you could)
I know this is an old threat but here is how to use Bitlocker in WinPE. Hope this helps anyone passing through…
http://social.technet.microsoft.com/Forums/en-US/configmgrosd/thread/4ca1dac3-d16b-4c2a-8c1e-5c13aa669bb0
Excellent post Michael. I just have a little issue, whenever we create that BDE partition, it seems like it gets marked as the “active” partition, therefore getting the “C:” letter in WinPE. We can always write a script that will scan thru the bootconfig to correctly get the Windows partition, but aside from this, is there any way to avoid this?
Thanks!
Basically no.. WinPE will add drivelers in the order it discovers the partitions… you can however use the variable OSDTargetSystemDrive it should point to the drive letter where the OS will be installed!
From my experience Winpe assigns drive letters to partitions based on size
300MB (partition 2) will get C: as it’s smallest.
I ran into an issue with this but had the problem when I was in windows with a different TSVariable –
http://myitforum.com/cs2/blogs/jconnor/archive/2011/03/12/setup-windows-and-configmgr-using-patch-quot-smstsmdatapath-fails-1635.aspx
Hello Jay,
Drive letters are assigned based on partition order 0=C:, 1=D:, 2=E:. When you create the System partition it becomes partition 0. This means it gets C: and the bigger OS partition 1 gets D:. But what to do for the Apply Operating System task? What I did for Refresh scenario was to check for a directory and set variable OSPART. Then set Apply Operating System to that variable.
Great post, thanks for the info.
Bitlocker can be disabled from Winpe, by adding WMI support into Winpe
[…] USMT 4.0, Hardlink and Bitlocker in SCCM OSD How can I do a backup of a machine, and keep the files on the encrypted drive, and then be able to […]
Thanks for a great post, this really relates to my customers environment!
But, when I add the Disable Bitlocker step at the top of the TS, I only get the errors:
The task sequence execution engine failed to executing the action (Disable BitLocker) with error code 50 (and error code 80070032 in the SMSTS.log)
Any tips would be appreciated!
I can’t seem to get a hardlinked USMT backup if a remote USMT backup has currently been done. The reason I want this is because I want a hardlinked USMT for all my machines, but a remote USMT done as an optional pre-step for VIP customers. It’s pretty much as a failsafe just in case the hard drive fails during an OS refresh. Do you have sample TS exports from Config Mgr?
Great post.
Some sample TS would be nice though. 🙂
I want to install win 7, how to using OSD only for drive C: without intruding other drive.
[…] 17. USMT 4.0, Hardlink and Bitlocker in SCCM OSD […]