In part 1, I talked about the requirements for Bitlocker and showed you how to extend your Active Directory Schema if you run Windows Server 2003 SP1/SP2 Windows Server 2003 R2 domain controllers. We then sat the permission so that a Windows 7 machine was able to write its own TPM owner password to Active Directory.
Today I am going to walk you through how to configure the Group Policy settings for Bitlocker which is required, in order to enable the backup of the Bitlocker recovery password and the TPM owner password, to Active Directory.
You will need either a Windows Server 2008 R2 or a Windows 7 machine with the Remote Server Administration Tools installed and the Group Policy Management Console enabled. Earlier operating systems do not have the required Group Policy extension and even though it is possible to copy the extensions to a Windows Server 2008 machine it is beyond the scope of this guide.
Group Policy Settings for Bitlocker Drive Encryption
Log on to a machine with the Group Policy Management console installed. You must use a domain administrator account or an account that has been delegated the permission required to create, edit and link Group Policy object.
1. Click on Start, Administrative Tools and then click on Group Policy Management
2. In the Group Policy Management Console, Expand Forest: Name-Of-Your-Forest, Domains and Name-Of-Your-Domain (i.e petfood.local), and Group Policy Objects
3. Still in the Group Policy Management Console, right-click the Group Policy Objects Node and select New
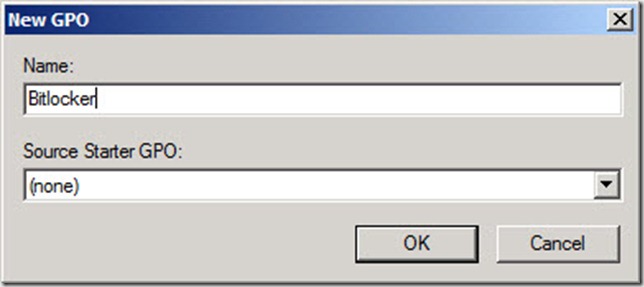
4. In the New GPO dialog box, type a name for the new Group Policy object, i.e. Bitlocker, and then click OK
5. In the Group Policy Management Console, under the Group Policy Objects node, right-click the GPO you just created, i.e. Bitlocker, and select Edit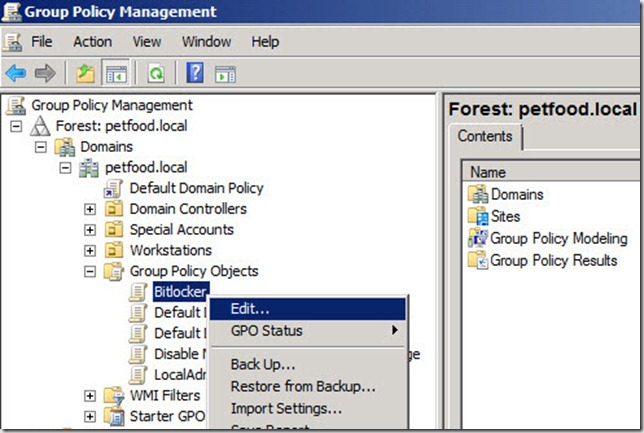
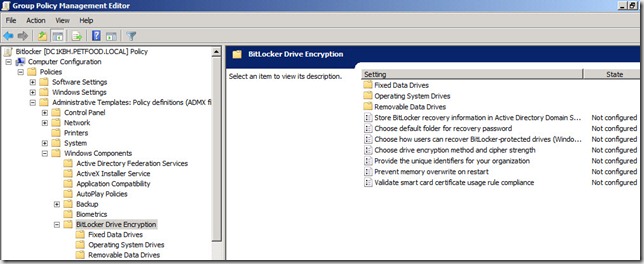
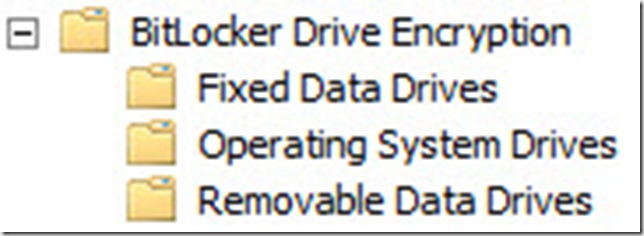
6. In the Group Policy Management Editor, expand Computer Configuration, Policies, Administrative Templates, Windows Components, Bitlocker Drive Encryption
7. Then click on the Operating System Drives node under the Bitlocker Drive Encryption node
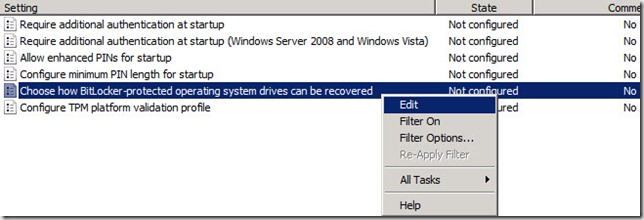
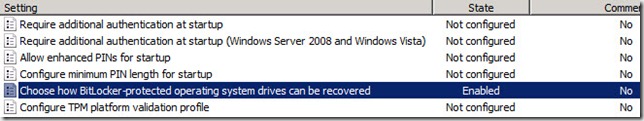
8. In the details pane of the Group Policy Management Editor, right-click the Choose how Bitlocker –protected operating system drives can be recovered setting and select Edit
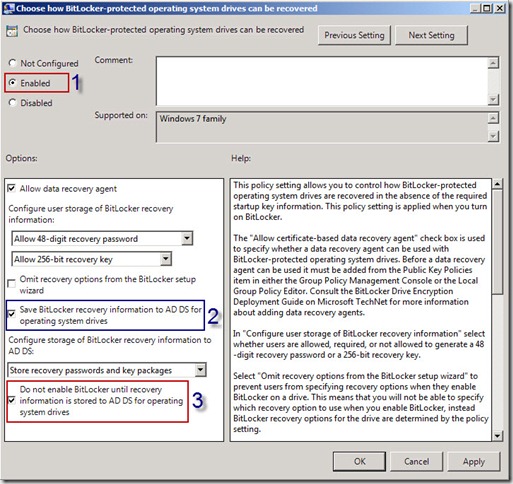
9. In the Choose how Bitlocker –protected operating system drives can be recovered windows, select Enabled (1)
10. Ensure that the textbox next to Save Bitlocker recovery information to AD DS for operating system drives (2) is selected
11. Select the checkbox next to Do not enable Bitlocker until recovery information is stored to AD DS for operating system drives (3)
12. Then click OK
13. Back in the Group Policy Management Editor, ensure that the State of the Choose how Bitlocker –protected operating system drives can be recovered setting says Enabled
Note: If you want to configure backup of Bitlocker recovery passwords for Fixed Data Drives and Removable Data Drives as well, you can do so by following the same steps you just performed
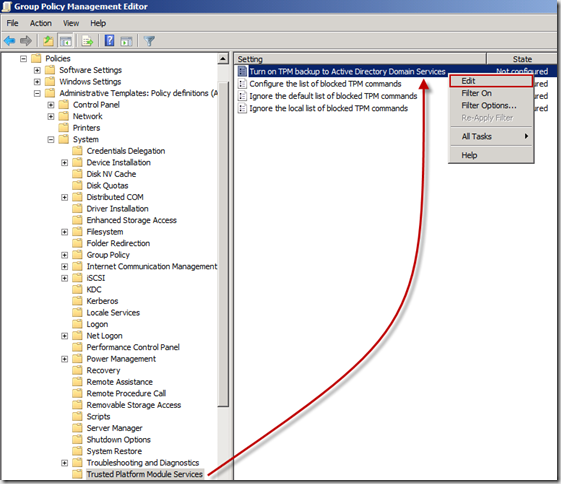
14. Still in the Group Policy Management Editor, expand the System node by clicking on the + sign next to it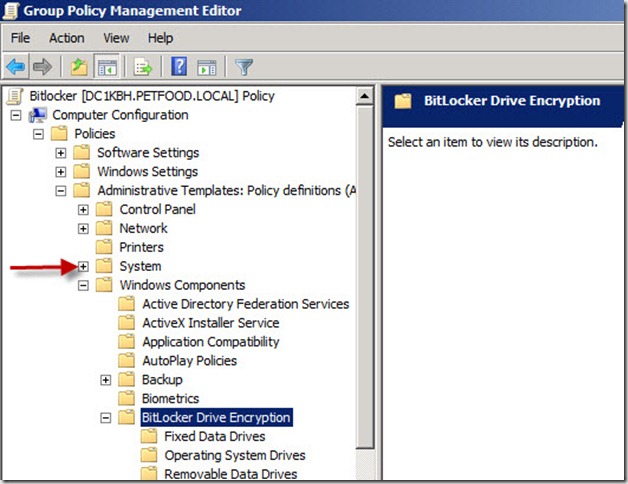
15. Under the System node, click on the Trusted Platform Module Services node and then in the details pane, right-click Turn on TPM backup to Active Directory Domain Services and select Edit
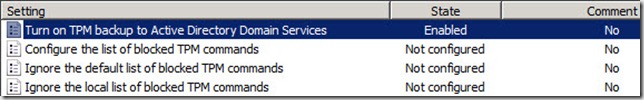
16. In the Turn on TPM backup to Active Directory Domain Services window, select Enabled (1)
17. Ensure that the textbox next to Require TPM backup to AD DS (2) is selected and then click OK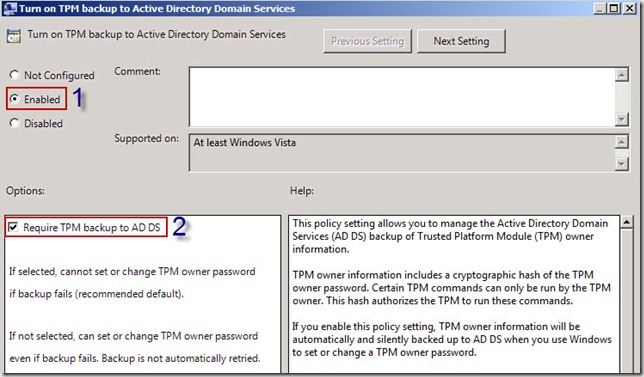
18. Back in the Group Policy Management Editor, ensure that the State of the Turn on TPM backup to Active Directory Domain Services setting says Enabled
19. Click on File and then select Exit to close the Group Policy Management Editor
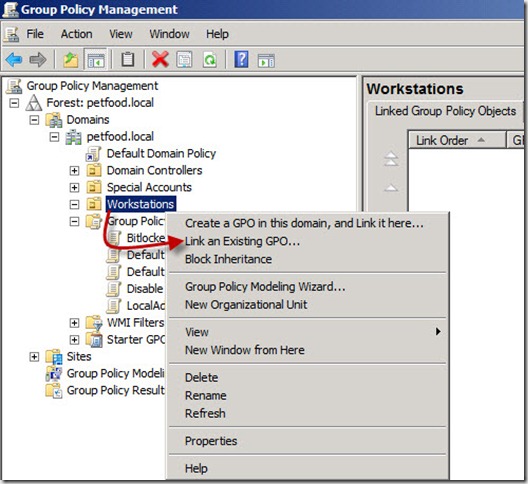
20. Back in the Group Policy Management Console, right-click the Organizational Unit (OU), i.e. Workstations, where you want the Group Policy settings you just configured to apply.
21. In the Select GPO window, click on the name of the GPO you just configured, i.e. Bitlocker, and then click on OK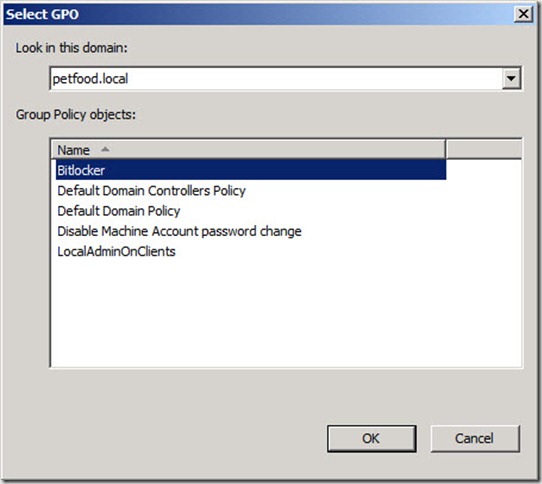
22. Verify that the GPO you just selected, i.e Bitlocker, is shown under the appropriate OU, i.e. Workstations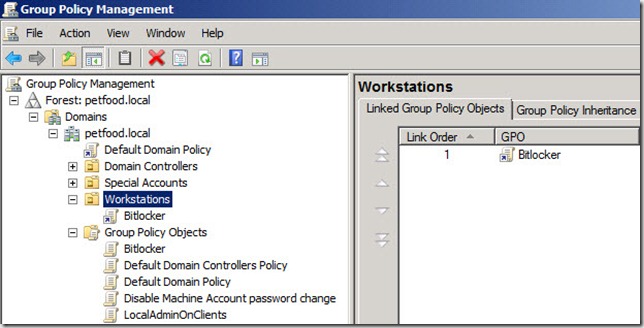
You have now enabled backup of Bitlocker recovery passwords and TPM Owner information to Active Directory and all you have to do is to place all the Windows 7 machine, on which you want to enable Bitlocker in the OU where you linked the Group Policy object.
In part 3 I will walk you through how to enable Bitlocker manually on a Windows 7 machine and more importantly how to find the Bitlocker recovery password using the BitLocker Recovery Password Viewer for Active Directory, and the TPM Owner password for a Windows 7 machine.



raspberry ketone max reviews
Coretech Blog » Blog Archive » SCCM Admins guide to preparing your environment for Bitlocker Drive Encryption – part 2
i assume part three never happened?
I think, maybe it didn’t work properly. So, there is no part 3.