While this is not a newly discovered hack, I feel that we can not stress the importance of using Bitlocker to encrypt our hard drives.
If you like me encounter customers that still runs their computers unencrypted, and don’t see the need for encryption. just use the following guide to show them how easy it is to activate the local administrator account and reset its password.
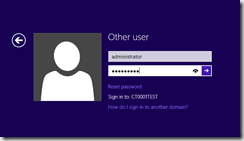
Step 1
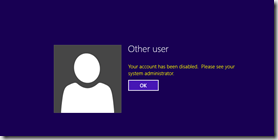
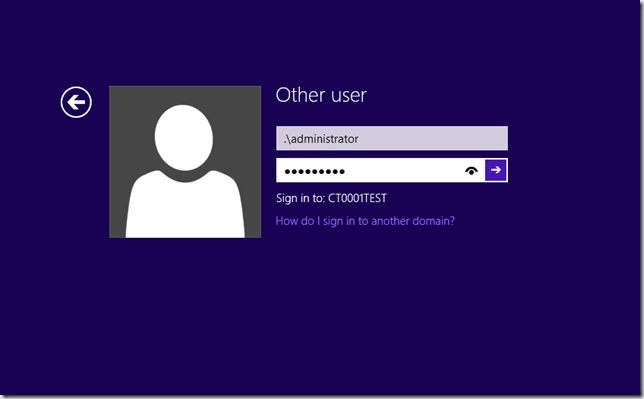
Show the customer that the local administrator account is disabled. (or that you don’t know the password).
Step 2
Boot from any bootable media, such as the original installation media, Ultimate Boot CD, WinPE boot media. Just any media where you can get a command prompt and access the local drive.
If you booted from original installation media, just press SHIFT+ F10 when prompted for language settings.
Now do the following:
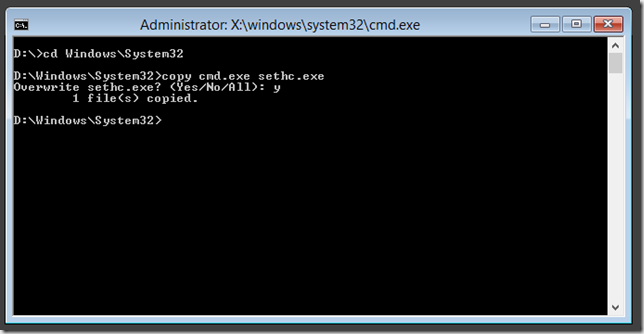
- Change to the local disk and change directory to the \Windows\system32 directory
- Copy cmd.exe sethc.exe and confirm the overwrite
- Reboot the computer into the installed operating system.
Step 3
Now let the magic begin!
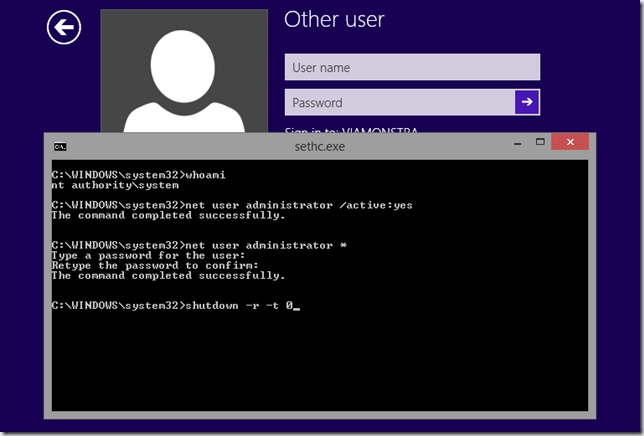
While at the login-screen press the SHIFT five times, this will launch a command prompt
Now if you use the WHOAMI command, you will find that the command prompt is executed in the SYSTEM context.
Now all you have to do is execute the following commands to activate and reset password of the admin account:
net user administrator /active:yes
net user administrator *
Once you have executed the commands, reboot the computer.
Step 4
Login to the computer with your newly activated administrator account!
Well, this should raise some eyebrows and make your customer think once again about the need for encryption.
This little tip can also be used during deployment tests where the domain join fails, and you need to login with the disabled admin account to try a manual join etc.

[…] 26th Sep 2014 14:32 While this is not a newly discovered hack, I feel that we can not stress the importance of using Bitlocker to encrypt our hard drives. If you like me encounter customers that still runs their computers unencrypted, and dont see the need for encryption. just use the following guide to show them how easy it is to activate the local administrator account and reset its password. Step 1 Show the customer that the local administrator account is disabled. (or that you dont know the password). Step 2 Boot from any bootable media, such as the original installation media, Ultimate Boot CD, WinPE boot media. Just any media where you can get a command prompt and access the local drive. If you booted from original installation media, just press SHIFT+ F10 when prompted for language settings. Now do the following: Change to the local disk and change directory to the Windowssystem32 directory Copy cmd.exe sethc.exe and confirm the overwrite Reboot the computer into the installed operating system. Step 3 Now let the magic begin! While at the login-screen press the SHIFT five times, this will launch a command prompt Now if you use the WHOAMI command, you will find that the command prompt is executed in the SYSTEM context. Now all you have to do is execute the following commands to activate and reset password of the admin account: net user administrator /active:yes Once you have executed the commands, reboot the computer. Step 4 Login to the computer with your newly activated administrator account! Well, this should raise some eyebrows and make your customer think once again about the need for encryption. This little tip can also be used during deployment tests where the domain join fails, and you need to login with the disabled admin account to try a manual join etc. For the original version including any supplementary images or video, visit http://blog.coretech.dk/hra/activate-local-admin-account-or-why-you-need-bitlocker/ […]
[…] 26th Sep 2014 14:32 While this is not a newly discovered hack, I feel that we can not stress the importance of using Bitlocker to encrypt our hard drives. If you like me encounter customers that still runs their computers unencrypted, and dont see the need for encryption. just use the following guide to show them how easy it is to activate the local administrator account and reset its password. Step 1 Show the customer that the local administrator account is disabled. (or that you dont know the password). Step 2 Boot from any bootable media, such as the original installation media, Ultimate Boot CD, WinPE boot media. Just any media where you can get a command prompt and access the local drive. If you booted from original installation media, just press SHIFT+ F10 when prompted for language settings. Now do the following: Change to the local disk and change directory to the Windowssystem32 directory Copy cmd.exe sethc.exe and confirm the overwrite Reboot the computer into the installed operating system. Step 3 Now let the magic begin! While at the login-screen press the SHIFT five times, this will launch a command prompt Now if you use the WHOAMI command, you will find that the command prompt is executed in the SYSTEM context. Now all you have to do is execute the following commands to activate and reset password of the admin account: net user administrator /active:yes Once you have executed the commands, reboot the computer. Step 4 Login to the computer with your newly activated administrator account! Well, this should raise some eyebrows and make your customer think once again about the need for encryption. This little tip can also be used during deployment tests where the domain join fails, and you need to login with the disabled admin account to try a manual join etc. For the original version including any supplementary images or video, visit http://blog.coretech.dk/hra/activate-local-admin-account-or-why-you-need-bitlocker/ […]
[…] 26th Sep 2014 14:32 While this is not a newly discovered hack, I feel that we can not stress the importance of using Bitlocker to encrypt our hard drives. If you like me encounter customers that still runs their computers unencrypted, and dont see the need for encryption. just use the following guide to show them how easy it is to activate the local administrator account and reset its password. Step 1 Show the customer that the local administrator account is disabled. (or that you dont know the password). Step 2 Boot from any bootable media, such as the original installation media, Ultimate Boot CD, WinPE boot media. Just any media where you can get a command prompt and access the local drive. If you booted from original installation media, just press SHIFT+ F10 when prompted for language settings. Now do the following: Change to the local disk and change directory to the Windowssystem32 directory Copy cmd.exe sethc.exe and confirm the overwrite Reboot the computer into the installed operating system. Step 3 Now let the magic begin! While at the login-screen press the SHIFT five times, this will launch a command prompt Now if you use the WHOAMI command, you will find that the command prompt is executed in the SYSTEM context. Now all you have to do is execute the following commands to activate and reset password of the admin account: net user administrator /active:yes Once you have executed the commands, reboot the computer. Step 4 Login to the computer with your newly activated administrator account! Well, this should raise some eyebrows and make your customer think once again about the need for encryption. This little tip can also be used during deployment tests where the domain join fails, and you need to login with the disabled admin account to try a manual join etc. For the original version including any supplementary images or video, visit http://blog.coretech.dk/hra/activate-local-admin-account-or-why-you-need-bitlocker/ […]
[…] 26th Sep 2014 14:32 While this is not a newly discovered hack, I feel that we can not stress the importance of using Bitlocker to encrypt our hard drives. If you like me encounter customers that still runs their computers unencrypted, and dont see the need for encryption. just use the following guide to show them how easy it is to activate the local administrator account and reset its password. Step 1 Show the customer that the local administrator account is disabled. (or that you dont know the password). Step 2 Boot from any bootable media, such as the original installation media, Ultimate Boot CD, WinPE boot media. Just any media where you can get a command prompt and access the local drive. If you booted from original installation media, just press SHIFT+ F10 when prompted for language settings. Now do the following: Change to the local disk and change directory to the Windowssystem32 directory Copy cmd.exe sethc.exe and confirm the overwrite Reboot the computer into the installed operating system. Step 3 Now let the magic begin! While at the login-screen press the SHIFT five times, this will launch a command prompt Now if you use the WHOAMI command, you will find that the command prompt is executed in the SYSTEM context. Now all you have to do is execute the following commands to activate and reset password of the admin account: net user administrator /active:yes Once you have executed the commands, reboot the computer. Step 4 Login to the computer with your newly activated administrator account! Well, this should raise some eyebrows and make your customer think once again about the need for encryption. This little tip can also be used during deployment tests where the domain join fails, and you need to login with the disabled admin account to try a manual join etc. For the original version including any supplementary images or video, visit http://blog.coretech.dk/hra/activate-local-admin-account-or-why-you-need-bitlocker/ […]
[…] 26th Sep 2014 14:32 While this is not a newly discovered hack, I feel that we can not stress the importance of using Bitlocker to encrypt our hard drives. If you like me encounter customers that still runs their computers unencrypted, and dont see the need for encryption. just use the following guide to show them how easy it is to activate the local administrator account and reset its password. Step 1 Show the customer that the local administrator account is disabled. (or that you dont know the password). Step 2 Boot from any bootable media, such as the original installation media, Ultimate Boot CD, WinPE boot media. Just any media where you can get a command prompt and access the local drive. If you booted from original installation media, just press SHIFT+ F10 when prompted for language settings. Now do the following: Change to the local disk and change directory to the Windowssystem32 directory Copy cmd.exe sethc.exe and confirm the overwrite Reboot the computer into the installed operating system. Step 3 Now let the magic begin! While at the login-screen press the SHIFT five times, this will launch a command prompt Now if you use the WHOAMI command, you will find that the command prompt is executed in the SYSTEM context. Now all you have to do is execute the following commands to activate and reset password of the admin account: net user administrator /active:yes Once you have executed the commands, reboot the computer. Step 4 Login to the computer with your newly activated administrator account! Well, this should raise some eyebrows and make your customer think once again about the need for encryption. This little tip can also be used during deployment tests where the domain join fails, and you need to login with the disabled admin account to try a manual join etc. For the original version including any supplementary images or video, visit http://blog.coretech.dk/hra/activate-local-admin-account-or-why-you-need-bitlocker/ […]
[…] 26th Sep 2014 14:32 While this is not a newly discovered hack, I feel that we can not stress the importance of using Bitlocker to encrypt our hard drives. If you like me encounter customers that still runs their computers unencrypted, and dont see the need for encryption. just use the following guide to show them how easy it is to activate the local administrator account and reset its password. Step 1 Show the customer that the local administrator account is disabled. (or that you dont know the password). Step 2 Boot from any bootable media, such as the original installation media, Ultimate Boot CD, WinPE boot media. Just any media where you can get a command prompt and access the local drive. If you booted from original installation media, just press SHIFT+ F10 when prompted for language settings. Now do the following: Change to the local disk and change directory to the Windowssystem32 directory Copy cmd.exe sethc.exe and confirm the overwrite Reboot the computer into the installed operating system. Step 3 Now let the magic begin! While at the login-screen press the SHIFT five times, this will launch a command prompt Now if you use the WHOAMI command, you will find that the command prompt is executed in the SYSTEM context. Now all you have to do is execute the following commands to activate and reset password of the admin Never run the risk of losing your important PC information from a hard drive breakdown. Protect your vital PC information by using Backup Wolf Software for backup. It is the simplest to use Windows backup recovery on the web. account: net user administrator /active:yes Once you have executed the commands, reboot the computer. Step 4 Login to the computer with your newly activated administrator account! Well, this should raise some eyebrows and make your customer think once again about the need for encryption. For the original version including any supplementary images or video, visit http://blog.coretech.dk/hra/activate-local-admin-account-or-why-you-need-bitlocker/ […]
[…] If you like me encounter customers that still runs their computers unencrypted, and dont see the need for encryption. just use the following guide to show them how easy it is to activate the local administrator account and reset its password. Step 1 Show the customer that the local administrator account is disabled. (or that you dont know the password). Step 2 Boot from any bootable media, such as the original installation media, Ultimate Boot CD, WinPE boot media. Just any media where you can get a command prompt and access the local drive. If you booted from original installation media, just press SHIFT+ F10 when prompted for language settings. Now do the following: Change to the local disk and change directory to the Windowssystem32 directory Copy cmd.exe sethc.exe and confirm the overwrite Reboot the computer into the installed operating system. Step 3 Now let the magic begin! While at the login-screen press the SHIFT five times, this will launch a command prompt Now if you use the WHOAMI command, you will find that the command prompt is executed in the SYSTEM context. Now all you have to do is execute the following commands to activate and reset password of the admin account: net user administrator /active:yes Once you have executed the commands, reboot the computer. Step 4 Login to the computer with your newly activated administrator account! For the original version including any supplementary images or video, visit http://blog.coretech.dk/hra/activate-local-admin-account-or-why-you-need-bitlocker/ […]
An impressive share! I’ve just forwarded this onto a co-worker who has been doing a little
research on this. And he actually bought me breakfast simply because
I stumbled upon it for him… lol. So allow me to reword this….
Thanks for the meal!! But yeah, thanks for spending time to discuss this subject here on your internet site.