When joining a computer to AAD either manually or by using a provisioning package, Bitlocker will be enabled automatically if your device has the necessary prerequisites. However in the case that Bitlocker is disabled this is how you enable Bitlocker, save the Bitlocker Key Protector to ADD (also known as the recovery key) and recover the key in the case you need it. So this blog post is both for the end-user and IT-pro I guess.
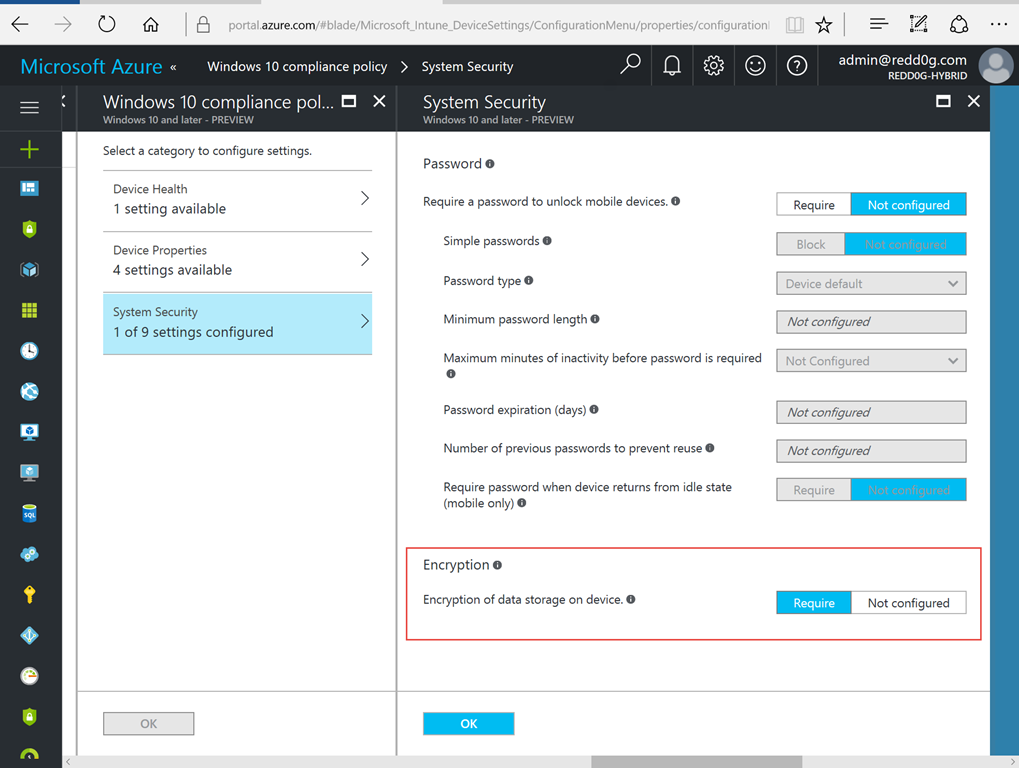
In this scenario we have configured a Device Compliance Policy in Intune where we require Encryption of data storage on devices and sent the policy to all Mobile Users. Like so…
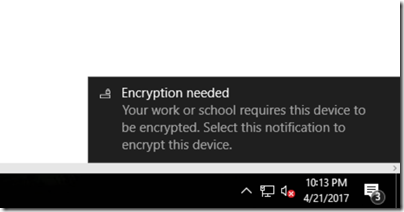
Now, from the user side, they will receive a notification that their device is not compliant with company policy and that Encryption is needed. Click on the notification to start Encryption process.
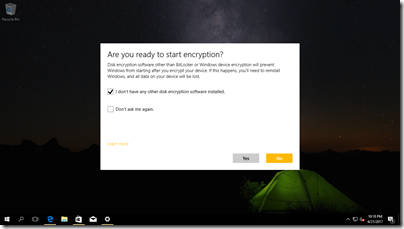
Make sure you do not have any other Device Encryption software installed and click Yes.
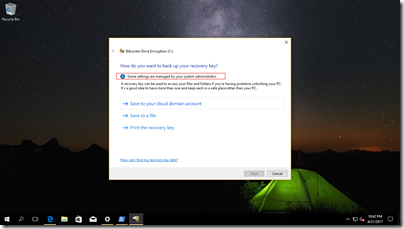
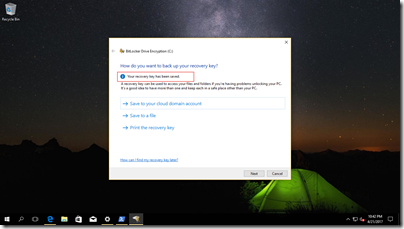
Make sure that you save the recovery key to your cloud account. You will be notified that the recovery key is saved.
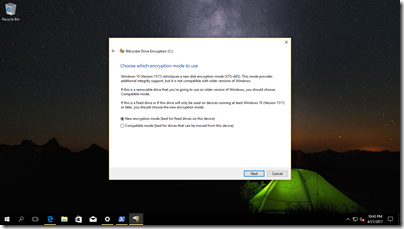
Choose the new Encryption mode (which is Xts Aes 128)
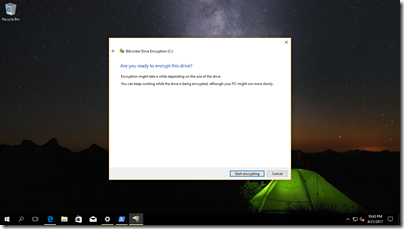
Start encryption and go to a long lunch. ![]() This can take some time… But know that you can work as normal alongside the encryption process.
This can take some time… But know that you can work as normal alongside the encryption process.
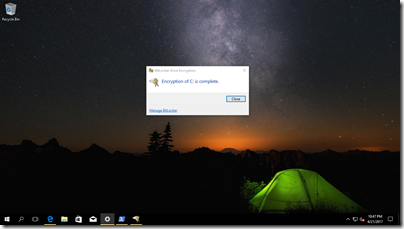
Confirm that the encryption process is complete.
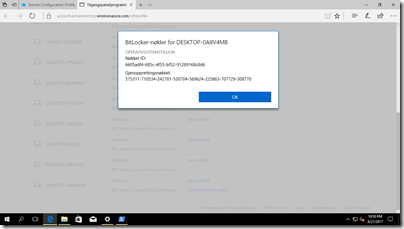
Now the encryption process is done and your data is secure. But how do we recover the drive in the case where we loose access to it. Well the key is stored in AAD and can be recovered easily by the end-user itself or by an administrator.
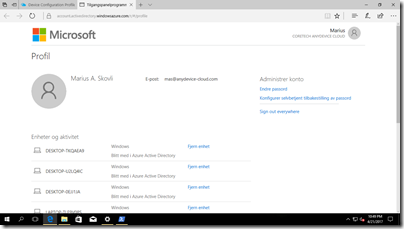
To retrieve the recovery key go to the following link and login with your corporate credentials (Work/School-account):
https://account.activedirectory.windowsazure.com/r/#/profile
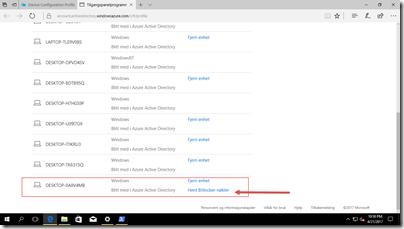
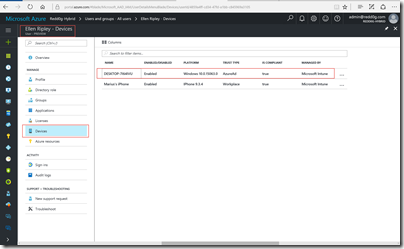
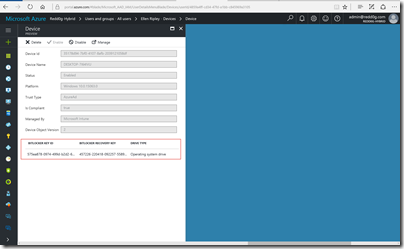
Find your computer by name and click on retrieve Bitlocker-keys
You can do the same in Azure Active Directory by going to https://portal.azure.com. Go to Users and Groups and search for the user.
And there you Go. There is no way to automate the Encryption process from Intune. But I hope we at some point will be able to execute PowerShell scripts, where we could automate the process. As far as I know only with Windows 10 1703 as the PowerShell commandlet BackupToAAD-BitLockerKeyProtector which you need to save the recovery key to AAD, is only in 1703 and up. If you want to experiment with PowerShell here is the script I created. It works and it simply does the same as the manual step above.
[sourcecode language='powershell' padlinenumbers='true'] Enable-BitLocker -MountPoint "C:" -EncryptionMethod XtsAes128 -UsedSpaceOnly -SkipHardwareTest -RecoveryPasswordProtector $BLV = Get-BitLockerVolume -MountPoint "C:" | select * BackupToAAD-BitLockerKeyProtector -MountPoint "C:" -KeyProtectorId $BLV.KeyProtector[1].KeyProtectorId [/sourcecode]
Stay tuned for more posts. ![]()
And do not forget to leave a comment if you have any questions.
/Marius
![image[64] image[64]](https://blog.ctglobalservices.com/wp-content/uploads/old/image64_thumb.png)



Nice Posting and nice cmdlet!
For bulk AAD joined devices that are not assigned to a specific user it also works using the cmdlet “BackupToAAD-BitLockerKeyProtector”. The venet log says successfully backed up. But how can we then access the recovery key? Any ideas?
Have you found a way to get a recovery key via PowerShell? In your step above (You can do the same in Azure Active Directory by going to https://portal.azure.com. Go to Users and Groups and search for the user), I do see the key, however I can’t copy it and can only view the entire key by hovering over it. I’ve looked through the new Azure AD Powershell Version 2 (https://docs.microsoft.com/en-us/powershell/azure/active-directory/install-adv2?view=azureadps-2.0), but nothing relating to getting the keys is listed.
… [Trackback]
[…] Find More Informations here: blog.ctglobalservices.com/windows-client/mas/how-to-manage-bitlocker-on-a-azure-ad-joined-windows-10-device-managed-by-intune/ […]
I have done the bitlocker encryption policy and successfully pushed the policy on Windows 10 machines.however, I would like to know when will the recovery key updatedin the azure portal or is there any specificsetting to be made to set the recoverypath for the key ?
Thanks,
Uday
The recovery key will be uploaded to AAD computer object when the User starts the encryption process. For allways on-connected-standby devices it will happen when they do the Azure AD Join.
I’m also in the need to access the azure ad synced bitlocker key in a programmatic way, but didn’t found any solution yet.
Your solution seems to assume that KeyProtector[1] is the recovery password. This isn’t always the case. I think this would be better:
$BLV = Get-BitLockerVolume -MountPoint “C:” | select *
$BackupPassword = $BLV.KeyProtectors|Where {$_.KeyProtectorType -eq ‘RecoveryPassword’}
BackupToAAD-BitLockerKeyProtector -MountPoint “C:” -KeyProtectorId $BackupPassword.KeyProtectorId
I have on-premises environment, and machines are sync to Azure AD. Devices(Windows 10 1803) showing up in Azure in two join types, “Azure AD registered” and “Hybrid Azure AD joined”. I as admin see users BitLocker keys when i select device that join type is “Hybrid Azure AD joined”. When I select identical device under join type “Azure AD registered”, BitLocker keys doesn’t showing up and because users are connected to devices through “Azure AD registered” join type they can’t see BitLocker keys in myapps.microsoft.com. Do you have any suggestions how i can display BitLocker keys under “Azure AD registered” devices?
Lucky you;
I`m in the same situation, but the second device account only shows MDM MS Intune, no Join type, both no registration date. And no recovery keys are shows at both devices. Even if I have set the BitLocker policy Save BitLocker recovery information to Azure AD as required
Dear Sir/Madam,
Is that possible to export a report for all users in AzureAD that their bitlocker recovery keys have been uploaded to Azure AD or not?
Thanks & Regards,
Kevin
Thanks. Very good article. I would be grateful if you could tell me what I’m doing wrong. Run Your script remotely via Enter-PSSession. This line says “BackupToAAD-BitLockerKeyProtector-Mount Point” C: “- KeyProtectorId $BLV.KeyProtector[1].KeyProtectorId” get “BackupToAAD-BitLockerKeyProtector : Catastrophic failure (Exception from HRESULT: 0x8000FFFF (E_UNEXPECTED))”. Perhaps You have thoughts on this?
Same here.
GOOD JOB!!!!
Great content useful for all the candidates of Windows Azure Training who want to kick start these career in Windows Azure Training field.
Windows is essential for all office devices.
Great Article. Thanks for sharing info.
Digital Marketing Course in Hyderabad
thanks for such an informative post you have shared
https://www.manishafashion.com/how-to-lose-weight-in-one-month/how-to-lose-weight-in-one-month-manishafashion-com/
Thanks for the information about bitlocker.
Is there a way of kicking off encryption using azure and bit locker during the imaging process for a new or reimaged machine instead of waiting for GP to see the machine?
In Windows Azure Profile it soley says “Workplace Joined” for my users. Before we rolled out Intune we could retrieve the Bitlocker Keys over the portal. Now the only show under devices for admins.
very nice blogs!!! i have to learning for lot of information for this sites…Sharing for wonderful information. Thanks for sharing this valuable information to our vision. You have posted a trust worthy blog keep sharing
Thank you for sharing this valuable content.
I love your content it’s very unique.
Thanks for this valuable information about bitlocker.
I’m also in the need to access the azure ad synced bitlocker key in a programmatic way, but didn’t found any solution yet.
First You got a great blog .I will be interested in more similar topics.I commend you for your excellent report on the knowledge that you have shared in this blog.
Your post is helping me a lot. Its really nice and epic. Thanks a lot for the useful info on this topic. You did it so much well. I love to see more about GBWhatsApp. Keep sharing and updating. Also share more posts with us. Thank you.
Thank for sharing
ABR Neuro Multi Specialty Hospitals Gynaecologist Doctor In Uppala Expert gynaecologist and obstetrician doctors in Uppala, Dr. Himabindu.N is a Gynecologist at ABR Multi-specialty Hospital. She is one of the young and dynamic doctors of Hyderabad.
Thanks a lot for the information.
Oncology Hospital in Hyderabad sreemanju hospital has been a leader in providing multispecialty tertiary healthcare across hyderabad, offering world-class, yet cost-effective clinical care, always keeping the patient’s The department has an experienced and efficient panel of doctors specialised in sub-fields of Medical Oncology, Haematology, Radiation Oncology, Specialised Once surgery and Bone Marrow Transplant services. Sreemanju hospital advanced cancer treatment and care using the latest equipment and technology.
Oncology Hospital in Hyderabad