Because The join domain account is often visible in your deployment answer file (unattend.xml of sysprep.inf) during the WinPE phase, it is important that this specific account does not have any more permission, than the bare minimum.. I often experience that a domain admin account is used for this job, which is a huge security breach. When i ask why this is, the answer is normally “ we can not find the information on how to create an account with only join domain rights”.
So her is a step by step guide on how to create such an account!
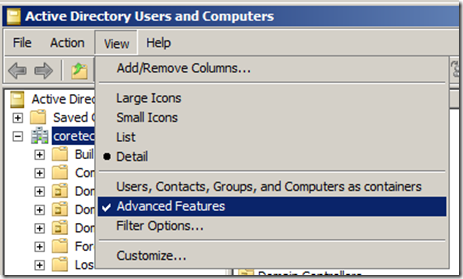
1. Open Active Directory Users and Computers and enable Advanced Features from the view menu
2. Create an account called sccmJD (or what ever you want to call it), and set password to never expire
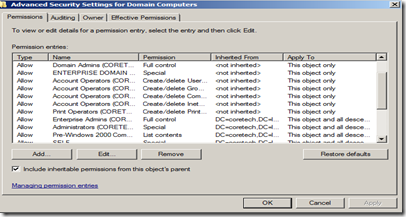
3. Right click the OU, you want the account to be able to join computer objects to (this could be the to level domain if you would like), and click Properties, open the Security TAB, and click Advanced.
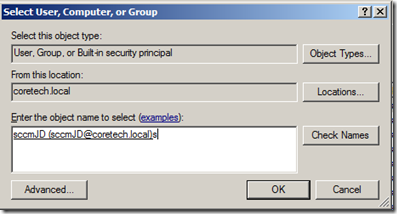
4: Click Add, and add the sccmJD account you just created, and click OK
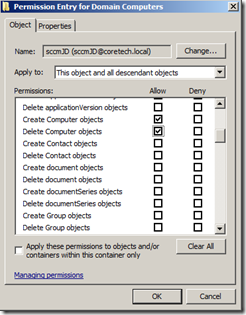
5: The Permission Entry for “OU” will appear. Make sure To set apply to : This object and all Descendant objects, and set Allow create and delete Computer objects. When done click OK.
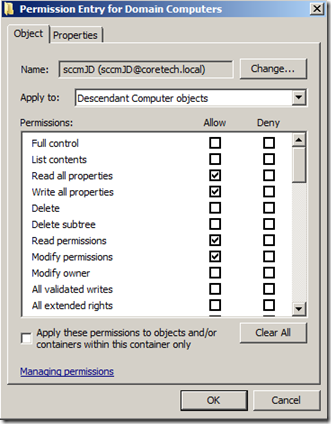
6: Repeat step 4 to add the sccmJD account again. Make sure To set apply to : Descendant Computer objects, and set Allow on:
Read All Properties
Write All Properties
Read Permissions
Modify Permissions
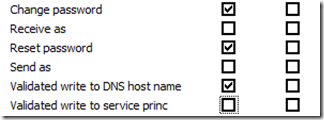
Change Password
Reset Password
Validated write to DNS host name
Validated write to service principal name
When done click OK.
7:Click OK twice to exit the permissions settings.
That should be it..



[…] […]
[…] http://blog.coretech.dk/mip/creating-a-joindomain-account-for-use-with-sccm-osd/ This entry was posted in System Center Configuration Manager. Bookmark the permalink. ← IIS – The HTTP headers are already written to the client browser. SCOM 2012 – Generate Alert from Log file → […]
If this is truly my solution, thank you!! We’ve been using my Admin account, which due to separation of duties, does not have the proper permissions to reuse accounts. Create, delete, rename – yes, but not all of the attributes necessary to reuse. We really were hoping not to have to delete all of the existing AD attributes.
[…] Coretech Blog » Blog Archive » Creating a JoinDomain account for use with SCCM OSD m.rasti [@] outlook.com پاسخ با نقل قول […]
در زیر تنظیمات مربوط به ساخت اکانتی جهت اتصال (Join) کامپیوترها به دامین توضیح داده شده است.
اکانت مربوطه فقط قابلیت اتصال دستگاهها به دامین را دارا بوده و هیچگونه دسترسی دیگری حتی ورود به دامین را دارا نمیباشد.
در زیر تنظیمات مربوط به ساخت اکانتی جهت اتصال (Join) کامپیوترها به دامین توضیح داده شده است.
اکانت مربوطه فقط قابلیت اتصال دستگاهها به دامین را دارا بوده و هیچگونه دسترسی دیگری حتی ورود به دامین را دارا نمیباشد.
1. Open Active Directory Users and Computers and enable Advanced Features from the view menu
On 2012? I cannot find:
Change Password
Reset Password
Validated write to DNS host name
Validated write to service principal name
@TDA
It’s there in 2012.
Probably you forgot to change “Applies to: Descendant computer objects”
I quite like reading a post that will make people think.
Also, thank you for allowing me to comment!
Hi! I could have sworn I’ve visited this web site before but after browsing through some of the articles I realized it’s new to me.
Anyhow, I’m definitely pleased I discovered it and I’ll
be book-marking it and checking back regularly!
[…] Which permissions are required at a minimum is already very well covered in this blog article: http://blog.coretech.dk/mip/creating-a-joindomain-account-for-use-with-sccm-osd/ […]
If you could remake or revise these instructions with screencaps from Server 2012R2, since it looks so much different, it would be extremely helpful.
Or Windows 10 even since it adds several permissions by default under Advanced
Thank,s. Just wath I was looking for!