First, I need to say….the new Cloud Management Gateway feature in Configuration Manager 1610 is awesome. There are a couple of gotchas you need to know about, when creating the service, but once you have overcome those hurdles – you will look like a hero at work, and be known as the person who finally enabled client management on internet based endpoints like road-warriors and colleagues working from home.
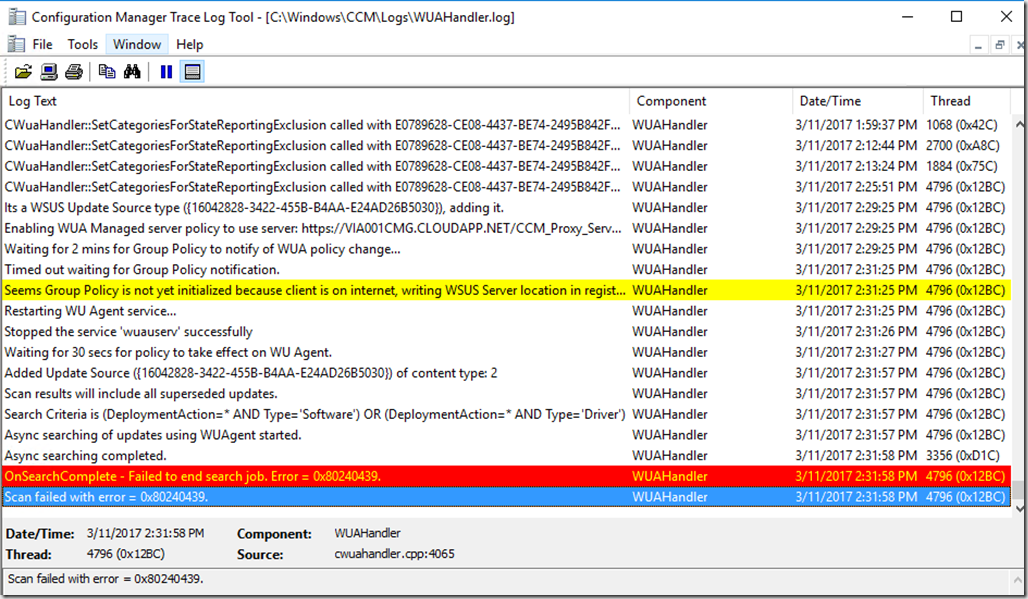
In the wuahandler.log on the client you might run into Scan failed with error = 0x80240439. If that happens, first step in your troubleshooting should be checking he configuration manager agent version and verify you have the latest version and hotfix installed.
Second step in troubleshooting is to check the IIS log files on the Software update point to see if the traffic makes it all the way from the client to your internal environment. If you don’t see any activity in your IIS log files, then the issue must be on the Cloud Management Gateway virtual machine in Azure.
- Login to Azure, select Cloud Services and find the CMG service.
- Enable remote desktop on the cloud management gateway
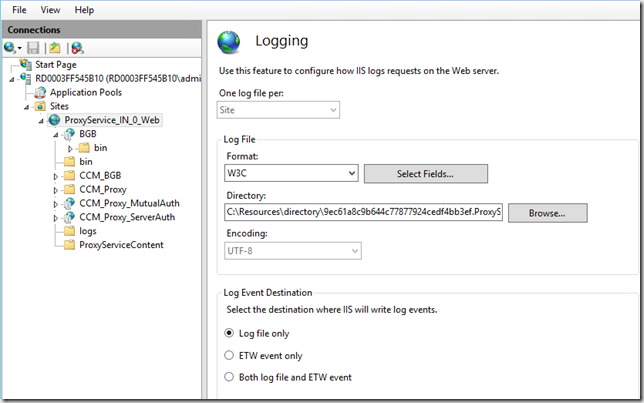
- Notice the IIS log files are not located in the default location
- Check the IIS log file for any errors related to software update traffic. In my example I have the following:
2017-03-13 07:00:39 W3SVC1273337584 RD00155D563B24 100.84.108.67 POST /CCM_Proxy_ServerAuth/72057594037927953/ClientWebService/client.asmx – 443 – 77.243.43.106 HTTP/1.1 Windows-Update-Agent/10.0.10011.16384+Client-Protocol/1.40 – – X000.cloudapp.net 413 0 0 357 14260 187
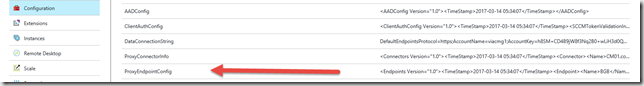
- In my example the error indicated that the traffic coming from the client was over the default limit which is why it never made back to my internal SUP server. You can check the default limits in Azure, connect to the cloud service and navigate to Configuration and check the ProxyEndpointConfig. Default value for ClientWebService</Name><ClientAuthScheme>0</ClientAuthScheme><RequestLimitContentLength>10240</RequestLimitContentLength> can be a little to low for some environments.
- In my DEMO environment, I had to modify the value in SQL by running this script
update Proxy_EndpointDefinition set RequestLimitContentLength=1048576 where Name=’ClientWebService’
- After running the script, the Cloud Manager component will write the configuration changes to Azure. You will be able to monitor the activity in the cloudmgr.log file on the site server and also by checking the updated ProxyEndpointConfig in Azure.
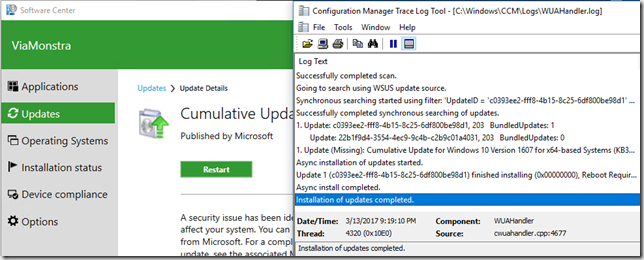
- For me the change took 2-3 minutes after which my clients started scanning for software updates and patched happily ever after
To those of you, who still believe a VPN connection is the way forward when managing clients on the road…….wake up, we are not in the 90’s any longer – stop it, it’s simply not cool.



This resolved my client WSUS scan failure on Windows 10 machines.
However i am still facing client scan failures on Windows 7 Machines.
Thanks Kent for this update.
Regards,
Rajul
I have to reinstall the Cloud Management Gateway to make it work. Thanks for the troubleshooting tips.
Rajul, are you saying that you deleted your existing Cloud Management Gateway and created a new one to resolve the issue? Or did you just remove the Cloud Management Gateway connection point role and reinstall the role? We’re still seeing this problem even with 1702 installed now. Hoping to figure this out soon!
Yeah I test with 1702 Branch and I have issues. Mine are 500 errors.
2017-04-17 18:12:01 W3SVC1273337584 RD0003FF2037A7 100.107.66.110 POST /CCM_Proxy_ServerAuth/72057594037937959/SimpleAuthWebService/SimpleAuth.asmx – 443 – 71.x.x.x HTTP/1.1 Windows-Update-Agent/10.0.10011.16384+Client-Protocol/1.40 – – xxxgw1.cloudapp.net 200 0 0 1557 789 203
2017-04-17 18:12:02 W3SVC1273337584 RD0003FF2037A7 100.107.66.110 POST /CCM_Proxy_ServerAuth/72057594037937959/ClientWebService/client.asmx – 443 – 71.x.x.x HTTP/1.1 Windows-Update-Agent/10.0.10011.16384+Client-Protocol/1.40 – – xxxgw1.cloudapp.net 500 0 0 1642 2022 218
Thanks for the fix, helped us out a lot! Keep up the great work.
Hi,I am getting this for device which connected from VPN. when device are not connected to VPN and avialable on internet so error will get remove. This happening with all device which are connecting through VPN.
NOTE: We don’t have any GPO
Group policy settings were overwritten by a higher authority (Domain Controller) to: Server https://XXXX.cloudmanagement.COM/CCM_Proxy_ServerAuth/72057594037927949 and Policy ENABLED WUAHandler 6/30/2020 12:47:25 PM 13420 (0x346C)
Failed to Add Update Source for WUAgent of type (2) and id ({282FA7BF-D8ED-485F-B22E-C8A896361F45}). Error = 0x87d00692. WUAHandler 6/30/2020 12:47:25 PM 13420 (0x346C)