I wrote a blog post back in April on “how to manage BitLocker on a Azure AD Joined Windows 10 Device managed by Intune”, where I also wrote a PowerShell script to automate the encryption process for the day that we would get PowerShell support in Intune. Well Microsoft announced in September the Management extension for Intune which basically lets you deploy PowerShell scripts via. Intune to Windows 10 devices. My co-worker Peter Daalmans wrote a great blog post about it right after, where he explained in more detail about the extension. I have a link for that post at the end of this page.
Now in this post I will show you have you can automate the BitLocker encryption process on Win10 devices and backup the protector to AAD Computer object that is managed by Intune, because there is no other way to automate the process for now. Remember to get this to work it is very important that your Disk Configuration layout properties and any other prerequisites is configured to get this to work. So I suggest, before you go any further that you read up on the following posts:
- BitLocker:
https://docs.microsoft.com/en-us/windows/device-security/bitlocker/bitlocker-overview
- Encrypted Hard Drive:
https://docs.microsoft.com/en-us/windows/device-security/encrypted-hard-drive
- Manage your Windows 10 devices via PowerShell and Microsoft Intune:
https://blog.ctglobalservices.com/powershell/pds/manage-your-windows-10-devices-via-powershell-and-microsoft-intune/
- How to manage BitLocker on a Azure AD Joined Windows 10 Device managed by Intune:
https://blog.ctglobalservices.com/windows-client/mas/how-to-manage-bitlocker-on-a-azure-ad-joined-windows-10-device-managed-by-intune
In order to do this, log on to https://portal.azure.com and go to you Intune Blade. Then move over to Device configuration and PowerShell scripts. Click on Add Script.
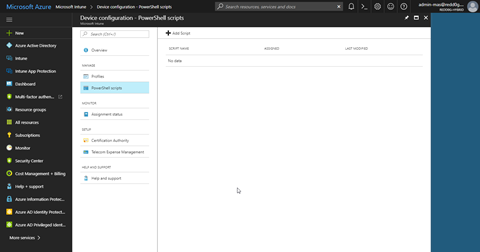
Give the script a name, description and then browse for the script. We do not need any furter configuration for the script, but if you want to you can have it run using logged on credentials and you can enforce a script signature check. But, we will just go ahead an click create.
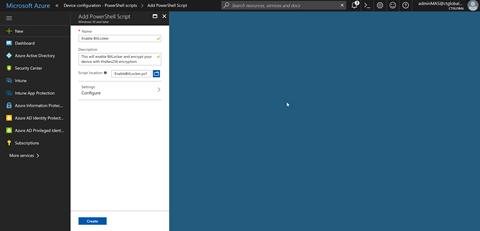
Next we need to assign the script to a user or computer group. I will assign it to a user group. When that is done click Save. And you are done.
Now, how will this actually look for the user? Well first and foremost the management extension will be installed shortly followed by the execution of the script itself! The encryption proccess will start immediately after.
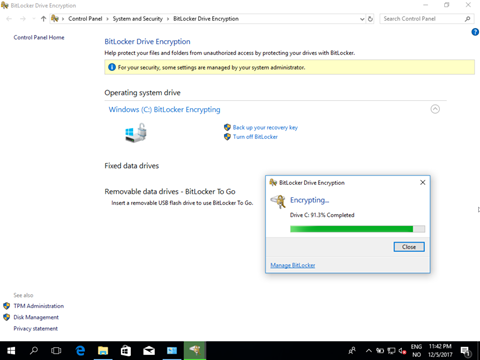
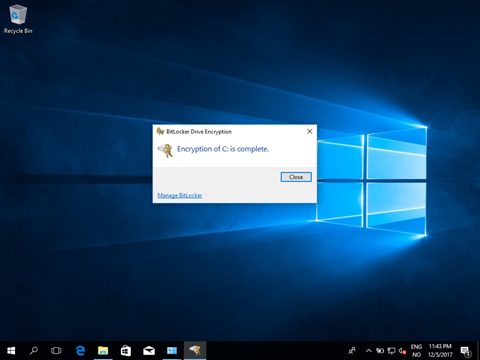
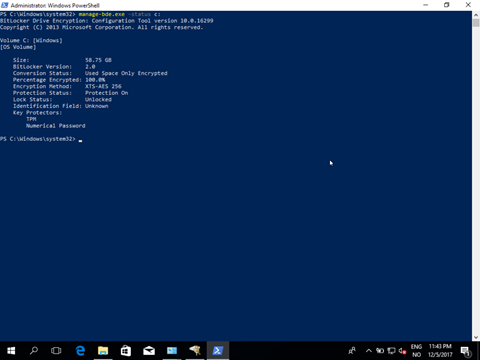
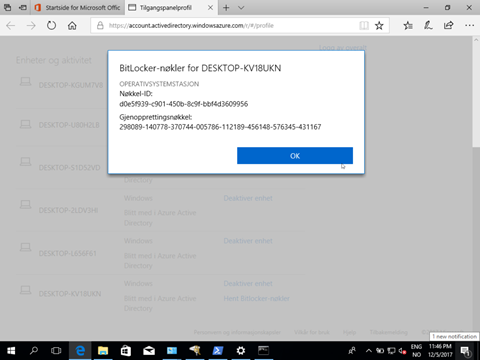
And the protector is safly stored on the computer Object in the cloud!
Here is the script:
Have a great December – a Merry Christmas and Happy New Year to you all!
Enable-BitLocker -MountPoint "C:" -EncryptionMethod XtsAes256 -UsedSpaceOnly -SkipHardwareTest -RecoveryPasswordProtector $BLV = Get-BitLockerVolume -MountPoint "C:" | select * BackupToAAD-BitLockerKeyProtector -MountPoint "C:" -KeyProtectorId $BLV.KeyProtector[1].KeyProtectorId


Hi Marius
Great write-up! I’m testing this in my lab and noticed that the assignment fails on Instant-Go systems. According to MS documentation for these type systems, if they’re AAD joined during OOBE, BitLocker will encrypt automatically. So once the assignment tries to execute on the device, encryption will already be in progress. If I try to run the BackupToAAD-BitLockerKeyProtector command, I get this error:
“The key protector specified cannot be used for this operation”
As a workaround, I modified your script to check if encryption/volume status is in progress first. If encryption is already in progress, it will exit out and the monitoring node for the device in Intune will show “Succeeded”.
The only other thing I noticed is that the encryption method on Instant-Go devices are set to XtsAes128.
Hi Phil / Marius,
I took a slightly different approach as I also wanted to cater for the scenario where clients were pre-provisioned for Bitlocker through an MDT/SCCM task sequence. We are building an OSD solution to re-purpose existing hardware to AutoPilot/Intune (Install OS / Drivers / Bios to UEFI / Language Packs and Sysprep). During the task sequence we use Bitlocker pre-provisioning to reduce the encryption time when the user enrols.
So rather than checking if encryption was in progress I just checked for two scenarios:
1. Volume encrypted and Protection Off (Pre-Provisioning)
or
2. Volume decrypted and Protection Off (not pre-provisioned or auto-encrypted)
For 1. I just resume Bitlocker and add the recovery password protector and for 2. I do the encryption as per the original script. Btw.. I also added support for detecting and ejecting removable or CD drives to prevent that from stopping the encryption process.
can you provide example code please?
awesome info. may I check what permission do i need to grant to the user locally inorder for it to upload the bitlocker key to azure?