Todays News is all about Petya – but the way it gets onto PCs and spreads across the network is actually old news.
In short, Petya does 3 things: Encrypt your files, Steal credentials, spread to other machines.
It takes advantage of the “Shadow Broker Vulnerability” MS17-010. If you have patched your machine, you will not be hit with the SMB exploit.
How ever it also use Mimikatz like capabilities to steal credentials from the local machine and copy it self to other machines $Admin share.
A kill-switch has been described as simple as creating a file called C:\Windows\perfc (without extension).
This should stop the current build of Petya.
If you want to stop the next version or next “ransomworm” there are a number of things you could do.
Almost 90% of the attacks share the same pattern of attack:
Disguised email with link to a malicious site or has an Office document with hidden macro.
User is tricked to open link or attachment and code is executed to a machine.
Depending on the goal and ingenuity of the malware writers, threats needs to be dealt with differently. You cannot just setup a solid email defense and leave it at that.
There are similarities in best practice approach to mitigate effectively against malware, regardless of the purpose of the malware. Lockheed Martin has defined a Security Framework: “CyberAttack Kill Chain”, which is a good way to discuss/analyse scenarios and security defenses.
There are 4 main phases.
“Delivery” – about getting in
“Exploit/Execution” – running code on the machine
“Lateral Movement” – traversing the network infecting other machines
“Action” – getting what they came for
Below are the phases and description on what Petya does and how you can protect yourself.
We know that a lot of companies are struggling making huge changes in their infrastructure to combat these attacks. Changes in infrastructure can be costly, can involve multiple business units and require end user training. A delay in making infrastructure changes can also cause a delay in implementing the defenses desperately needed. The fact that so many organizations still haven’t applied the MS17-010 Update from March speaks for it self.
I’ve tried focusing on solutions that are relatively easy to implement, but still raise the security bar significantly. But if you want the best security, you would need more.
Delivery
Attack
<edit> As some pointed out, Petya or NotPetya initially came from the Ukrainian Medoc patching mechanism. Downloading patch with Petya code and from there spreading using Shadow Broker Vulnerability” MS17-010 and steal credentials to move laterally. As story evolved, there are reports on different attack vectors where email with xls and hta is among them. Close to 90% of Ransomware and Malware in general is delivered through email, this must be a priority to strengthen defenses here.</edit>
- Petya use “Shadow Broker Vulnerability” MS17-010 to spread to your machine
- 85-90% of Malware is delivered to business as an Email with attachment or link to malicious code.
- Email filtering with inadequate inspection, not detecting obfuscated code and not able to track what embedded links points to.
- Result is that it is allowed to pass the inspection being delivered to the users mailbox.
Prevention
- Update all your windows machines with MS17-010
- Disable SMBv1 This is the currently most used method for spreading across the network. Use https://blogs.technet.microsoft.com/staysafe/2017/05/17/disable-smb-v1-in-managed-environments-with-ad-group-policy/
- E3 Exchange Online/O365 Advanced Threat Protection has SafeLink and SafeAttachment with sandbox analysis.
- Most attacks are likely to be stopped with Spam settings SPF Hard fail, as sender is usually spoofed.
- Consider adding a HTML disclaimer on emails coming from outside, to raise awareness to users.
![]()
Exploit/Execution
Attack
- Petya is reported to be hidden in an Office document – as a macro – that will launch Explorer.exe and drop files to %temp%. This is a very common approach with phishing or malware attacks.
- I will attempt to launch subprocesses encrypting files and spreading to other machines.
Prevention
- Reported kill-switch for Petya is to place an empty file as C:\Windows\perfc
- Device Guard will effectively prevent unknown executable code from executing. Takes planning, testing and training.
- Consider using GPO w/Software Restrictions or AppLocker as a first step of lockdown approach. Easier to implement, but don’t let it replace Device Guard implementation plans!
- Prevent users from launching applications directly from %TEMP%, %APPDATA% and %PROGRAMDATA% – Even some applications has issues, very few are business related (Spotify etc.)
- Remove users Administrator rights, Use “Access Director” if your business is not able to accept completely taking away permissions. (www.basic-bytes.com)
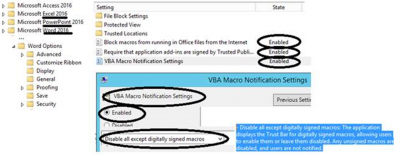
- Macro settings should be locked down
- – Must be enabled for all Office apps
- – Block macros from running in Office files from the Internet (if there is a business justification sender need their macros to be signed)
- – Require signing for Application add-ins
- – Remove the Trust bar for any unsigned macros (will also disable the macros)
Lateral movement
Attack
- Exploit steal credentials using Mimikatz functionality, copy files to network shares, using CVE-2017-0144/MS17-010 vulnerability to spread to other machines.
- Currently it is hardcoded to use builtin wmic.exe by explicit path and drops a variant of psexec.exe renamed to dllhost.dat (among other names)
Prevention
- Update all your windows machines with MS17-010
- Again: Device Guard is the most recommended security mitigation, but takes planning, testing and training
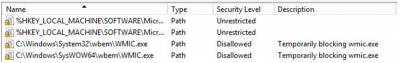
- Consider using GPO w/Software Restrictions / Applocker to block wmic.exe This process is hardcoded into Petya and this process is not in use by an average user, even if this is just to do damage control here and now.
- Using Local Administrator Password Solution to create a unique passwords for each server and workstation in the domain, effectively stops the ability to reuse credentials.
- Create accounts for administering end client machines. Create a Group Policy for denying local logon for server/domain admin accounts to any workstation that is used for reading email and browsing internet. Admin credentials should not be exposed to any end user workstation.
- Enable Credential Guard in Windows 10 – isolating credentials, so it is no longer possible to extract passwords from lssas.exe process and read cached credentials.
- Ensure your W2008R2 and W7 machines has Backport patch KB2871997 installed and has Group Policies in place to “Prevent local users from accessing from network”.
- Segment your network. Create GPO firewall block rule to block Client-to-Client traffic on TCP139 and TCP445 “. But verify that you don’t have applications that has client-to-client communication requirements.
- Disable SMBv1 This is the currently most used method for spreading across the network. Use https://blogs.technet.microsoft.com/staysafe/2017/05/17/disable-smb-v1-in-managed-environments-with-ad-group-policy/
- Detect and investigate using Windows Defender Advanced Threat Protection. Where did it come from?, Where did it spread to? Block processes and isolate machines (if Windows 10 1703)
Action
Attack
- Once exploit has been able to run, new PE executable files are launched to start the encryption and attempt to steal credentials saved on local machine
Prevention
- Device Guard again! see a pattern?
- Lock down the ability to run executables directly from %TEMP%, %APPDATA% and %PROGRAMDATA% using GPO Software Restrictions / Applocker
- Remove users Administrator rights Use “Access Director” if your business is not able to accept completely taking away permissions. (www.basic-bytes.com)
- Detect credential passing using Microsoft Advanced Threat Analytics. The Mimikatz like functionality use pass the hash to access $admin shares on surrounding machines. MS ATA will detect this for you.
As I mentioned, there a much more into protecting an environment with all the varieties in the CyberAttacks. Hope above give you input on how to protect yourself from getting hit by this and the next threat.
/Steven Wood
@StevenWDK



merci bcq