after a good discussion at TechNet (Read here), i think we have reached a solution that works.
Problem:
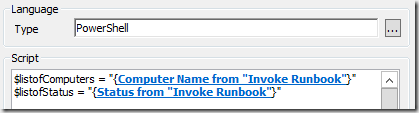
When we are running PowerShell in Orchestrator using published data we insert it directly into the script.
This means that part of the input can contain characters that is able to run malicious code, or just break the script.
f.x. if we use double quotes (") around the input, and the input contains a double quote, it will break the script.
Solution:
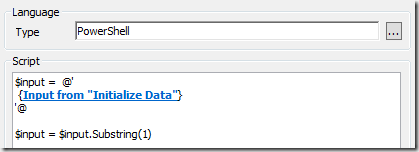
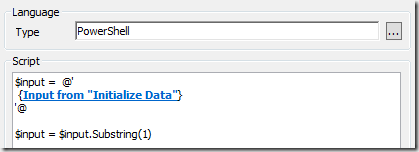
Use single quote here-string and make sure that your syntax follows this example:
[System.String] $retrievedUserInput=@’
<insert space><insert published data here>
‘@
$input = $input.Substring(1)
The important part is to use the single quote here string and make sure to insert and extra space before the published data
you can more info about here strings here
(Notice: This is my own suggestion of best practice)


Hi Jakob
Thanks for sharing the information. but this does not really solve all crafted input. This one can still run.
$string = @’
‘@; get-service;sfasdfa
sdfasdfa
‘@ ; get-service ; @’
‘@
input publish data could not line break and next line they could close the ‘@; before issuing the injected statement.
Cheers
Deepak