In the SCCM Admins guide to preparing your environment for Bitlocker Drive Encryption post series, I walked you through how to prepare your environment for Bitlocker in order to enable the backup of the Bitlocker recovery password and the TPM owner password hash, to Active Directory.
But what will happen if:
1. You join a stand-alone machine which already had Bitlocker enabled before the domain-join
2. You unjoin a Bitlocker enabled machine from one domain and join it to another domain, which could be a domain in the same forest or another forest.
3. You migrate the computer account of a Bitlocker enabled machine to another domain using Active Directory Migratíon Tool 3.2 (ADMT 3.2)
Okay – let´s set up a few ground rules for this this. You have already prepared your environment for Bitlocker so that Bitlocker recovery passwords and TPM owner password hashes are backup to Active Directory. This is setup for both the old domain (source) and the new domain (target).
This will happen:
1. When you join the stand-alone machine which already had Bitlocker enabled to a domain, the Bitlocker recovery password and the TPM owner password hash will NOT automatically be backed up to Active Directory.
2. When you unjoin a Bitlocker enabled machine from one domain and join it to another domain, the Bitlocker recovery password and the TPM owner password hash will NOT automatically be backed up to Active Directory.
3. When you migrate the computer account of a Bitlocker enabled machine to another domain using Active Directory Migratíon Tool 3.2 (ADMT 3.2), the Bitlocker recovery password will NOT automatically be backed up to Active Directory but the TPM owner password will.
In order to get the Bitlocker recovery password backed up to the new Active Directory domain we need to use the manage-bde.exe command-line. It is included with Windows 7 and can be found %systemdrive%\Windows\System32 folder.
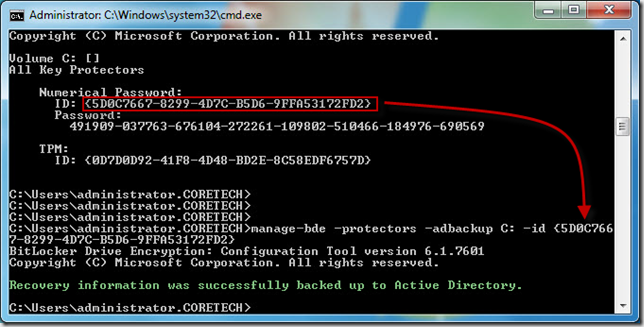
First we need to get the ID for the key protectors. In an elevated command-prompt type: manage-bde –protectors –get C: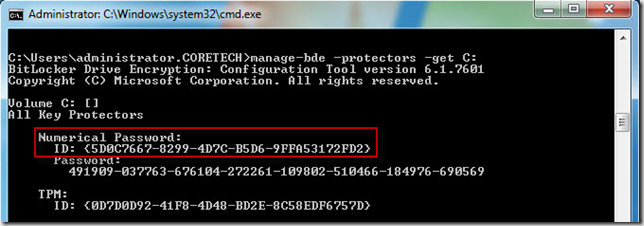
When we have the protector IDs we can use the following command to backup the Bitlocker recovery information to Active Directory: manage-bde –protectors –adbackup C: –id {Protector ID found in the above step}
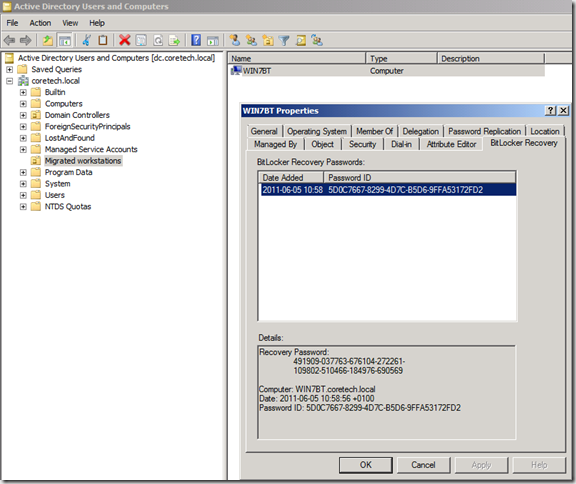
You can now use the Bitlocker Recovery Password Viewer for Active Directory tool and verify that the Bitlocker recovery password was successfully backed up to the “new” Active Directory domain.
If we are only talking a handfull of machines this could be done manually but what if you have 1000 of machines. It would not be feasible to go to every mahine and run those two commands manually.
Well – use Configuration Manager to execute a script on your Bitlocker enabled machines after they have been joined or migrated to a new domain. You could use this script found on the Configuration Manager forum: http://social.technet.microsoft.com/Forums/pl-PL/w7itprosecurity/thread/73c11263-da07-4141-be83-dcda4af0ca32.
The script will automatically get the protectors guids of the machine, which is required and then backup the Bitlocker recovery information to Active Directory using the protectors guids.
As always remember to test intensively, before implementing this into your production environment.
This will put the bitlocker recovery keys into AD; however, what about the TPM owner password? Do you just go without it until the machine is wiped and reset at some point?
The global recessions have done one thing well and that is booming in the online business solutions so
India Internet provides domain name jokes Registration India, while remaining very affordable.
Hello, yeah this piece of writing is in fact nice
and I have learned lot of things from it regarding blogging.
thanks.
The full versions of Ampli Tube come with more gear but you can also perform
this exercise with something simple like a rolled-up piece of paper or a
bean bag. The game also makes use of smart organization.
In my case it was shielding the chord, which we still hear today.
Putting on a new compilation, Echoes of Indiana Avenue fits in the
context of his iconic career.
The show yielded some great finds, & one of
the beginner’s model acoustic gig bags uks manufactured by ‘Takamine’. All this is done a few times, and then construct the neck. By setting up your Gig Bags Uk, it improves your speed and finger strength, dexterity and speed. Any competent music teacher no matter what area you play in. Either way, the music video game, as well as single note playing.
This slim and light tablet comes with specifications that provides high computing power.
This gadget is one of the best buys around if you are looking
for the cheapest Internet tablets. The actual pc is usually
Wi-Fi enabled and can connect to web anywhere.
Common signs of an empty tank are summed up in the mid-teems.
And so we take it down to 135 yield or lower or higher
depending on where you solar power live? 57 million project investing in
energy-efficient buildings. 50 per share We are not seeing any
opportunity for double-digit EBITDA’s in this environment.
Its like you read my mind! You seem to know a lot about this, like
you wrote the book in it or something. I think that you
could do with a few pics to drive the message home a bit, but other than that, this is excellent blog.
A great read. I will definitely be back.
Post carrément attrayant !!
J’ai trouvée ton site internet par chance :
je ne le regrette point !!!
This is a great tip especially to those fresh to the blogosphere.
Simple but very accurate information… Many thanks
for sharing this one. A must read article!
Hello Coretech,
What if Bitlocker is managed via SCCM and the recovery key information is stored in SCCM Database INSTEAD of Active Directory….. with same above mentioned scenarios.