This post is the first in a 3 part series describing how you prepare your environment for Bitlocker Drive Encryption. We will look at the requirement for Bitlocker and how you extend your Active Directory Schema if you run Windows Server 2003 SP1/SP2 Windows Server 2003 R2 domain controllers. If you run Windows Server 2008 or Windows Server 2008 R2 do not worry. Your job just got a “lot” easier because the schema in those two versions of the operating already has the bitlocker extensions.
We will then set the permission so that a Windows 7 machine is able to write its own TPM owner password to Active Directory.
In part 2 and 3, we will be configuring the Group Policy settings required for enabling Bitlocker Drive Encryption and test-drive the configuration by enabling Bitlocker manually on a Windows 7 client and lastly test that we can recover the Bitlocker password and TPM Owner password from Active Directory.
The SCCM admins guide to preparing your environment for Bitlocker Drive Encryption series overview:
- Part 1: Bitlocker requirements, preparing your Windows Server 2003 SP1/SP2 environment and setting the requirement permission for backing up TPM owner passwords.
- Part 2: Configure the Bitlocker Group Policy settings
- Part 3: Enabling Bitlocker and recover Bitlocker password and TPM owner password from Active Directory (coming soon)
Bitlocker requirements
You have verified the following on all computers where you intend to enable Bitlocker Drive Encryption:
- The computer has the latest firmware (BIOS)
- The BIOS is configured correctly and the TPM Module is enabled
- That the computer has a compatible Trusted Platform Module (TPM) version 1.2 or later
You also need to ensure that you have a domain controller running at least Windows Server 2003 SP1 or later and have a working Active Directory Domain.
You have a version of Windows 7 that supports Bitlocker. You will need either the Enterprise or Ultimate edition of Windows 7.
You intend to store Bitlocker recovery passwords in Active Directory.
You have a Windows 7 computer joined to your domain where you have installed Remote Server Administration Tools (RSAT) or you have a Windows Server 2008 R2 computer joined to your domain. This is required in order to configure the Bitlocker Group Policy settings used for enabling Bitlocker Recovery password backup to AD DS.
Please note: The configuration of the above requirements are NOT included in this guide.
Preparing your Windows Server 2003 SP1 environment (Windows Server 2003 domain controllers only)
Important:
You should only perform the following steps if:
- All of your domain controllers are running Windows Server 2003 SP1, Windows Server 2003 SP2 or Windows Server 2003 R2
- You haven´t upgrade your schema in order to prepare for a Windows Server 2008 or Windows Server 2008 R2 upgrade.
If you have a least one domain controller running Windows Server 2008 or Windows Server 2008 R2 you must skip these steps and continue with the step described under the required permissions for backing up TPM owner information heading. The schema extensions required to support backup of BitLocker and TPM passwords in Active Directory are already present on these systems.
First you need to download the schema extensions (BitLockerTPMSchemaExtension.ldf) from: http://archive.msdn.microsoft.com/bdedeploy/Release/ProjectReleases.aspx?ReleaseId=3272
- Log on to a domain controller with an account that is member of the Schema Admins group
- Open a command-prompt and change directory to where you have placed the downloaded BitLockerTPMSchemaExtension.ldf file
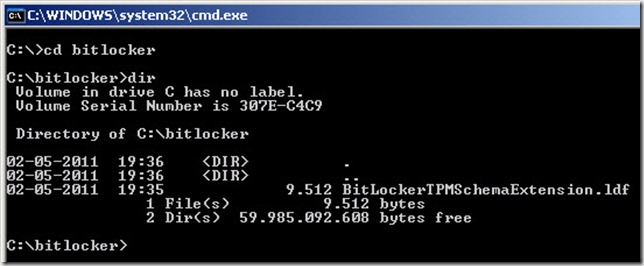
- Still in the command-prompt windows type:
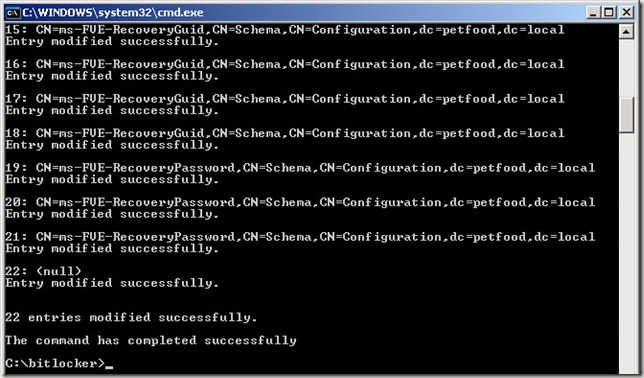
- ldifde -i -v -f BitLockerTPMSchemaExtension.ldf -c “dc=X” "dc=DomainName,dc=TLD" -k –j . To run this command in the petfood.local domain you would type: ldifde -i -v -f BitLockerTPMSchemaExtension.ldf -c “dc=X” "dc=petfood,dc=local" -k –j .
- Important: This command should be entered as one line. The trailing period (.) is part of the command
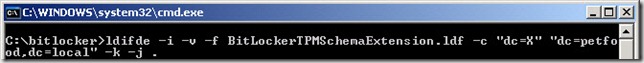
- Verify that the command completed successfully. 22 entries should be modified.
- You can find a log file in the directory where you executed the command called ldif.log. This file will give you detailed information about the operation.
Set the required permissions for backing up TPM owner information
Windows 7 can back up BitLocker recovery information (Bitlocker Recovery Password) under the computer object’s default permission.
The TPM Owner password information for the Trusted Platform Module (TPM) can be automatically backed up to Active Directory. This information allows an administrator to remotely manage the TPM.
Configuration Manager 2007 and MDT 2010 create a random TPM Owner password as part of enabling bitlocker. By design, a hash of the TPM password is saved in Active Directory and not the actual TPM password itself.
Windows 7 machines cannot back up the TPM owner information unless additional permission is added to the domain.
First you must download the Add-TPMSelfWriteACE.vbs script from here: http://archive.msdn.microsoft.com/bdedeploy/Release/ProjectReleases.aspx?ReleaseId=3205
- Log on to a domain controller with an account that is member of the Domain Admins group
- Open a command-prompt and change directory to where you have placed the downloaded Add-TPMSelfWriteACE.vbs file
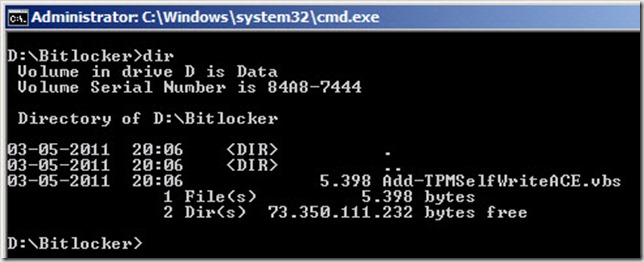
- In the command-prompt you just opened type: cscript Add-TPMSelfWriteACE.vbs
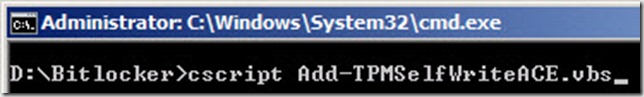
- Verify that the script returns a SUCCESS! message and then close the command-prompt.
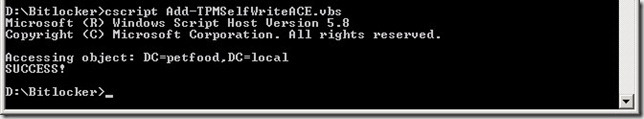
Verifying the permissions set by the Add-TPMSelfWriteACE script in Active Directory
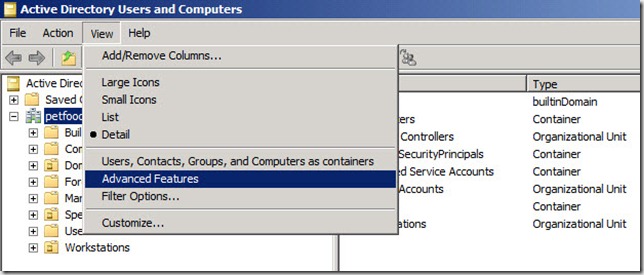
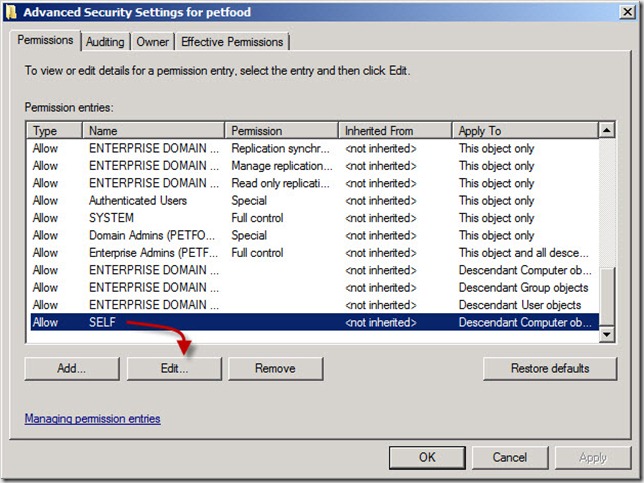
- On a computer where Active Directory Users and Computers snap-in is installed, click on Start, Administrative Tools, Active Directory Users and Computers (ADUC).
- In the top menu of the Active Directory Users and Computers snap-in, click View and then click on Advanced Features in the drop-down menu
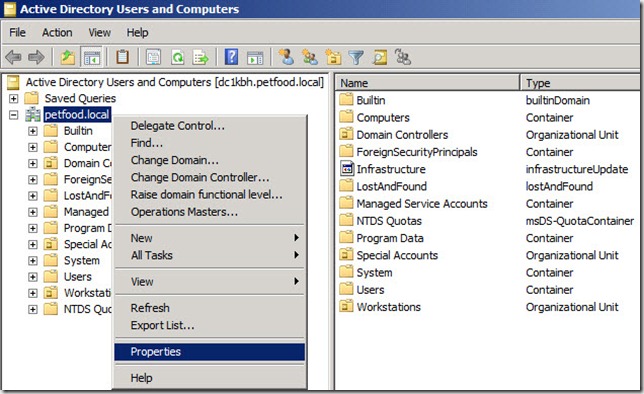
- Still in the ADUC snap-in, right-click the name of your domain i.e petfood.local and select Properties
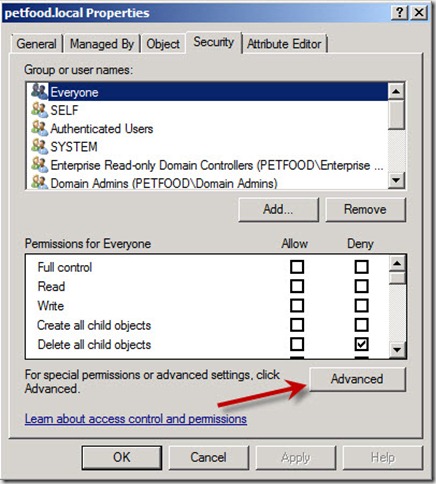
- In the name-of-your-domain Properties window i.e petfood.local, click on the Security tab and then click on the Advanced tab in the bottom of the window
- In the Advanced Security Settings for name-of-your-domain Properties window i.e petfood.local, scroll down to the last Allow SELF entry in the list and click on the Edit button
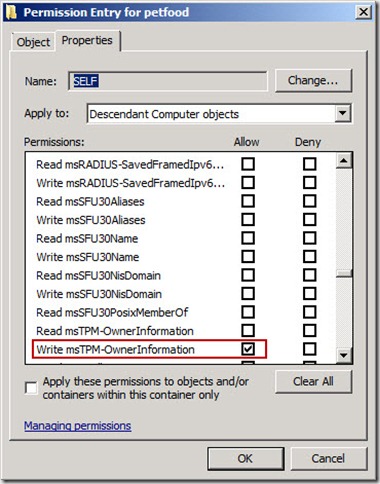
- In the Permission Entry for name-of- you-domain Properties window i.e petfood.local, under Permissions verify that the Allow checkbox next to the Write msTPM-OwnerInformtion enrtry is selected and then click OK three times
- Note: You have now verified that SELF (the computer itself) has the required permissions to write to the ms-TPM-OwnerInformation attribute for computer objects in the domain.
That´s it for part 1. Stay tuned for part 2 where we are going to configure the Group Policy settings required for enabling Bitlocker Drive Encryption.



Thanks, great info.
Hi,
great article. There is not much you can find on internet about mbam. I do have a problem though. Client encryption fails right after it starts saying that one or more drives couldnt be encrypted and contact bla bla. Can you please help me with that ?
Thanks
Asking questions are in fact pleasant thinjg iff you are not understandding anything entirely, except this article offers nice understanding even.
Read the Full Posting
Coretech Blog » Blog Archive » SCCM Admins guide to preparing your environment for Bitlocker Drive Encryption – part 1