In the following weeks I will blog about the some of the different 3rd. party software update solution we can integrate with Configuration Manager. I will focus my articles on:
- Installation of the product
- Richness of the update catalog
- Configuration Manager integration
- Approving Updates
- Deploying Updates
- Reporting
- How to get started
First I will test drive Secunia, a world-leading provider of Vulnerability Intelligence. Secunia has been around since 2002 and is most known for its award winning product CSI – Corporate Software Inspector.
The installation
Secunia requires a few components that are all easy to install and configure:
- The CSI console requirement
- https : // * . secunia.com must be added to trusted sites in your browser
- Adobe Flash plugin is need to display charts
- TCP port 443 open to the Internet
- Agent requirements
- Port 443/TCP open outbound
- Windows Update Agent
- Agentless monitoring or Secunia scan agent
The installation process is fairly simple, a few steps and you are presented with the main console.
Richness of the catalog
The catalog is built based on the data returned by scanning clients. You can perform an online scanning or download and install the Secunia agent. In my test I performed the online scan which revealed that I missed the latest Adobe Flash Player update. Using the technique requires that you can perform a scan of all clients on the network to ensure that all missing updates will be part of your future deployment. It’s not a big problem; but still something you must have as part of your software update planning.
The first process of scanning a system is to collect specific META data from primarily .EXE, .DLL, and .OCX files. This data is collected and then sent to Secunia’s Secure Data Processing Cloud (DPRC) where it is processed and parsed. After being processed, the data is matched against the Secunia File Signatures, which are the rules that matches the raw META data to an actual program installation.
Part of this matching process also results in an exact version being extracted from the META data. This means that after the initial parsing the Secunia CSI knows exactly which programs are on the system and their exact version. The inventory of software is then compared against the unique Secunia Advisory & Vulnerability Database, which contains the most accurate Vulnerability Intelligence. The result is a precise inventory of programs, their versions, and the exact security state of each of the programs, along with a direct reference to the corresponding Secunia Advisory, detailing the exact vulnerabilities and their Secunia assessed criticality and impact. Since the scan process works by looking at the actual files on the system being scanned, the result is extremely reliable as a program obviously cannot be installed on a system without the actual files being present.
Above is taken from the Secunia installation and configuration guide
Configuration Manager integration
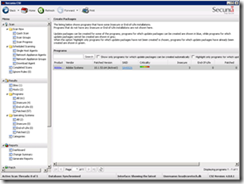
Once missing updates are found they will listed in the Secunia console. Creating the patch is a straight forward proces and requires a few clicks.
Double-click on the update to start the patch creation wizard
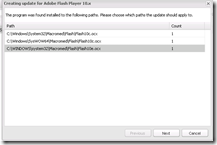
Select the Update and click Next
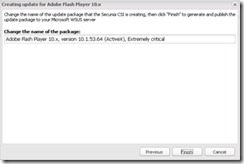
Before you publish the update you have the option to change the name. Click Finish to publish the Update to WSUS
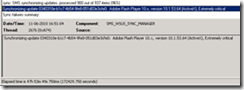
Above is the wsyncmgr.log file on the site server. The Adobe Update will automatically be imported into Configuration Manager during the next WSUS synchronization process.
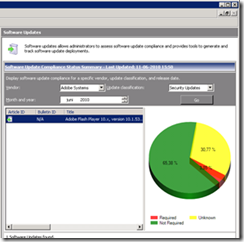
My Adobe update is available in the Configuration Manager console. The software update process is now the exact same as deploying a normal Windows Update.
How to get started
To get yourself started you’ll need to invest a little time in installing and getting to know the Secunia Management Console. You can download a trial version from http://secunia.com/vulnerability_scanning/corporate/trial/ – and then use the reference code BS.
It took me 10 minutes to get the console downloaded and installed. After 10 more minutes I was ready to deploy my first software update with Configuration Manager – pretty impressive 🙂
Originally posted to http://scug.dk/blogs/configurationmanager/archive/2010/06/22/integrate-3rd-party-software-update-with-configuration-manager-2007-and-secunia-part-i.aspx June 22nd. 2010