The new Cloud Management Gateway is going to make a big difference in the way we manage endpoints away from home in the future. The feature is a System Center Configuration Manager 1610 pre-release feature. Being a pre-release typically means = a little troubleshooting is required to get the feature working in different environments. In my previous blog post I described an issue with software update scan failing. The troubleshooting steps used in this blog post, are similar what I have described there.
In this environment we have a PKI with a Sub CA, and as part of the certificate upload somehow the certificate chain was broken (and yes, there is a script that describes how to upload the cert).
Client errors
In this example the error message in ccmmessaging.log (on the Internet client) was:
Post to https://MyCMG.CLOUDAPP.NET/CCM_Proxy_MutualAuth/72057594037928257/ccm_system/request failed with 0x87d00231.
a couple of things to check when this happen:
- From a client, open IE and see if you can browse to https://MyCMG.CLOUDAPP.NET. if you get an error like 403, something is broken and you need to dig into the IIS log files on the Azure box.
- Enable remote desktop on the cloud management gateway, and open the IIS log files to investigate further. In this example the log file had several lines like the one below. This error indicates
2017-03-14 09:15:47 W3SVC1273337584 RD00155D81000 IPadr CCM_POST /CCM_Proxy_MutualAuth/72057594037928257/ccm_system/request – 443 – IP adr HTTP/1.1 ccmhttp – – mycmg.cloudapp.net 401 0 0 1589 3928 78
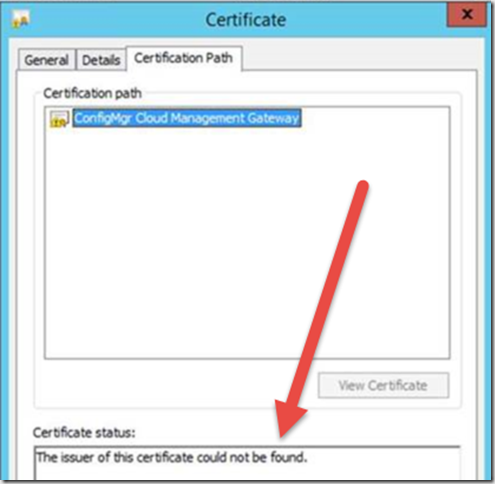
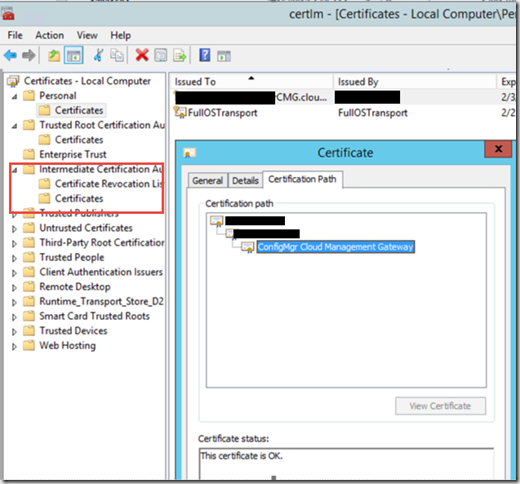
- Next step in troubleshooting is opening the certificate manager snap-in and check the computer store. In here your CMG certificate chain should include the correct certificate chain. as you can see in the illustration, the issuer of this certificate can’t be found, and as such our trust is broken.
- To fix the issue, copy and import your missing root certificate(s) to the Azure cloud management gateway server. The certificates are to be imported to the Intermediate Certification store. The correct way to get this done, is by running the script as described in this blog post – https://docs.microsoft.com/en-us/sccm/core/clients/manage/setup-cloud-management-gateway. If you upload the certificate manually it might be overwritten during maintenance of the virtual machine in Azure.
After that, check you ccmmessaging log and you should see traffic floating – once again………VPN is not really the way forward in the world of modern device management ![]()




Hi Kent,
I have an issue with my CMG and IIS showing 403.16 errors, my CMG has a trusted root certificate in the Intermediate store but the CMG server itself myservername.cloudapp.net server signing certificate is saying “The issuer of this certificate could not be found”
What would cause this? Thank you for your help
Hello Kent,
I did what you have detailed here but am still seeing “The Issuer of this certificate could not be found”. Any help on what else you may have done to solve thus?
You might have multiple issuing certificate servers. In that case all certs must be uploaded
We only have 1 cert server. Is there anything else you had to do besides running the thumbprint script to get it to show the correct path?
Log into the server in Azure, open the cert MMC and verify both cert are there
If i add the certs through Azure – they disappear after running the script (on the SCCM database) and still show just the 1, instead of the 3 total certs. What can be causing them to disappear? I am assuming i have to add them through Azure, then also manually and ALSO run the script.
Do I also have to add the SubCA certs to the “CMG” portion on the SCCM server under the properties of the CMG? It currently only shows the master, should i also be adding the SubCA’s?
Yes, you need the entire cert chain
Do you know how to get more than one cert added when it says browse instead of certificates?
Looking at the link you provided here: blog post – https://docs.microsoft.com/en-us/sccm/core/clients/manage/setup-cloud-management-gateway.
When I get to the client cert add part. Click Certificates to add client trusted root certificates. Add up to two trusted root CAs, and four intermediate (subordinate) CAs.
My version doesn’t say certificates, it says browse.
I’m not sure which came first. I’ve seen both on the web.
Do you know of any way to get past the 2 root, 4 intermediate CA limit? We have multiple domains and CAs. If a client has been issued a PKI cert then it does not seem to be able to use Azure for authentication. Mpcontrol.log indicates that it needs full cert chain…so unless clients are allowed to fail over to use Azure I need to be able to add more than 2 root CAs and 4 intermediate.